

Rewterz Threat Alert – APT Group SideWinder
January 8, 2020
Rewterz Threat Alert – Snake Ransomware Targeting Business Networks
January 8, 2020
Rewterz Threat Alert – APT Group SideWinder
January 8, 2020
Rewterz Threat Alert – Snake Ransomware Targeting Business Networks
January 8, 2020Severity
Medium
Analysis Summary
A series of sales-themed emails with IMG attachments. with purpose to deliver the NetWire RAT. A total of 15 emails carrying the same attachment were observed coming from two unique senders.
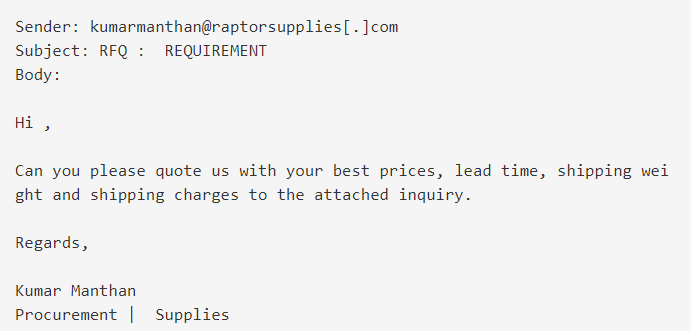
Email 1
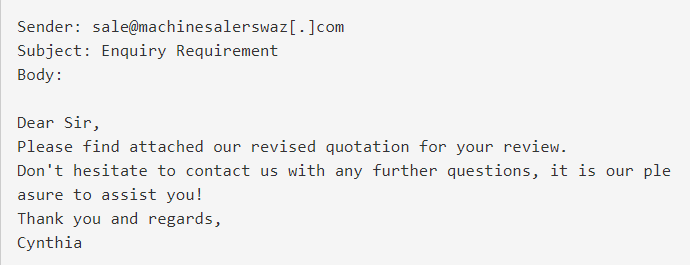
Email 2
In both cases, the referenced attachment is an IMG file named “Sales_Quotation_SQUO00001760.img.” Opening this file extracts an executable that we identified to be the NetWire RAT. Once executed, the malware establishes persistence via a scheduled task. Additionally, Registry keys are created to store the C2 server IP and install data of the RAT. Communication with the C2 server is performed over port 3012.\
Impact
Exposure of sensitive information
Indicators of Compromise
Email Subject
- Enquiry Requirement
- RFQ : REQUIREMENT
From Email
- kumarmanthan[@]raptorsupplies[.]com
- sale[@]machinesalerswaz[.]com
SHA-256
- 01b4694a473b86231293cc81b67be7bc813cd7ce58af39b72ea9e06652528444
- a943161c1b1e9ff7b2844a413c57f60641da782cf208c799bb4f13191fe7397d
Remediation
- Block all threat indicators at your respective controls.
- Always be suspicious about emails sent by unknown senders.
- Never click on the links/attachments sent by unknown senders.








