

Rewterz Threat Alert – FTCode PowerShell Ransomware Resurfaces in Spam Campaign
October 3, 2019
Rewterz Threat Advisory – Moxa EDR 810 Series Multiple Vulnerabilities
October 3, 2019
Rewterz Threat Alert – FTCode PowerShell Ransomware Resurfaces in Spam Campaign
October 3, 2019
Rewterz Threat Advisory – Moxa EDR 810 Series Multiple Vulnerabilities
October 3, 2019Severity
Medium
Analysis Summary
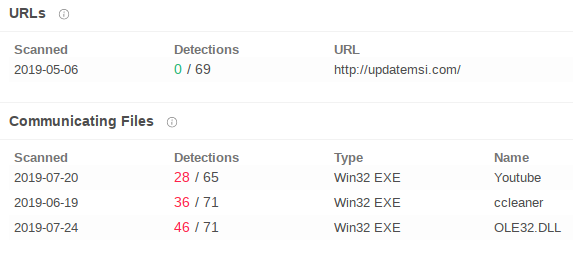
Exploiting a path traversal vulnerability of winrar, a Molerats spear phishing campaign is discovered. It is suspected that a Gaza Cybergang group is behind the campaign. At first step, the victim installs a downloader in their operating system which then gets infected with a RAT (Quasar). The downloader typically first tries to connect to a geo location domain and then the RAT is downloaded. The given hostname serve as C2 for the molerat. There are currently three samples that contact these domains given in the IoCs, while the URL itself is marked safe.
Impact
Data Theft
Indicators of Compromise
IP(s) / Hostname(s)
- myexternalip[.]com
- updatemsi[.]com
Email Address
lujyayman1000[@]gmail[.]com
Malware Hash (MD5/SHA1/SH256)
- cb65ded99393122d46d10439ebc39d25d258e60614170123923eeb066263ef2a
- bb019265a536a5e9a766dee97a2f3a82
- a3b9acf59907522a84bdb3e57f16b563aff0f43bdb7be2ac33037fab1f00bcf2
- a7994ae6ab70e5ee78c0857cfda498de
- cab43c760a21b4b33475b56cf511b20af65f828b5f051bde6bad78574c596cd2
- 4a1cd5442856184ea632434e15c4393f
- 0c4aa50c95c990d5c5c55345626155b87625986881a2c066ce032af6871c426a
- 3f67231f30fa742138e713085e1279a6
- 118d0bd8ec35b925167c67217d2fe06ac021ce253f72d17f1093423b8f9b4a2b
- 78845962f3006e3dbbc113afa8fff078
Remediation
- Block the threat indicators at their respective controls.
- Do not download email attachments coming from untrusted sources.
- Do not download any files from random sources on the internet.
- Keep winrar updated to the latest patched versions.








