

Rewterz Threat Alert – Phishing Attack Targeting United Nations and Humanitarian Organizations
October 31, 2019
Rewterz Threat Advisory – CVE-2019-18226 – ICS: Honeywell equIP and Performance Series IP Cameras and Recorders Authentication Bypass Vulnerability
November 1, 2019
Rewterz Threat Alert – Phishing Attack Targeting United Nations and Humanitarian Organizations
October 31, 2019
Rewterz Threat Advisory – CVE-2019-18226 – ICS: Honeywell equIP and Performance Series IP Cameras and Recorders Authentication Bypass Vulnerability
November 1, 2019Severity
Medium
Analysis Summary
The Maze Ransomware is conducting a new spam campaign that targets Italian users by pretending to be the country’s Tax and Revenue Agency. The Maze Ransomware is not a new infection, but within the past month it has been picking up steam with new campaigns, partnering with exploit kits, and inserting playful comments targeting researchers in their executables.
According to security researcher JAMESWT, users in Italy are being targeted with spam emails pretending to be from the Italian Revenue Agency, or the Agenzia delle Entrate, which is responsible for collecting taxes and revenue for the government.
These emails contain a subject of “AGGIORNAMENTO: Attivita di contrasto all’evasione. Aggiornamento” and contain a word document called “VERDI.doc”, which allegedly contains new guidelines that businesses and citizens must follow.

If a user opens the attached VERDI.doc they will be told that the file is encrypted using RSA encryption and that they must “Enable Content” in order to properly view it.
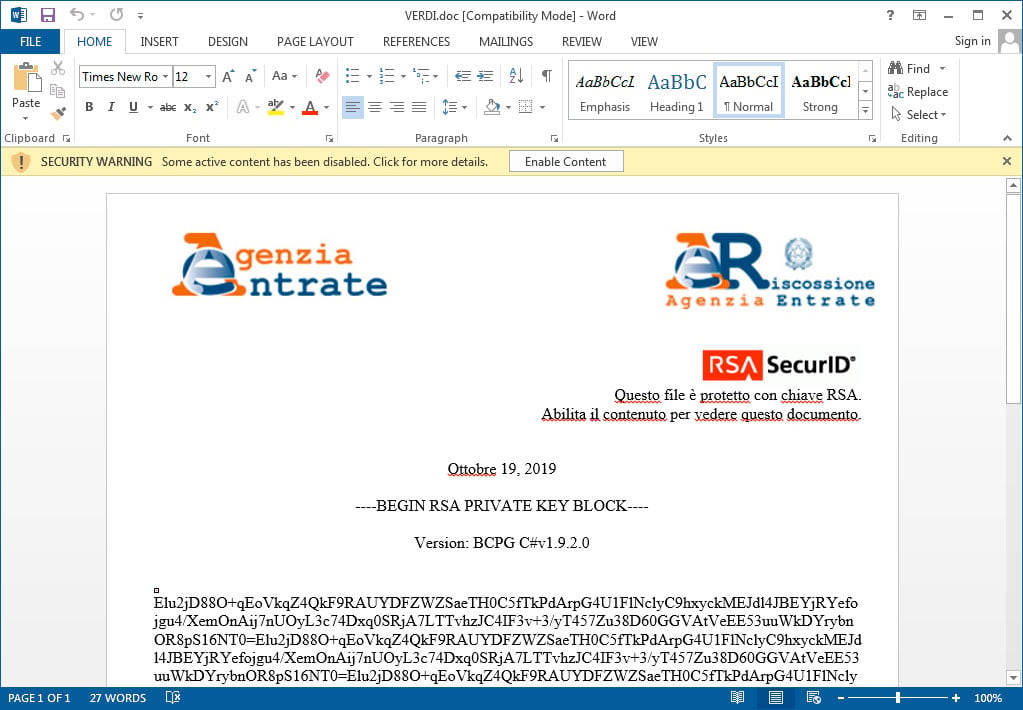
Malicious Word Document
If the user enables the content, an embedded macro will be executed that downloads the ransomware to C:\Windows\Temp\wupd12.14.tmp file and executes it.
Impact
File encryption
Remediation
- Always be suspicious about emails sent by unknown senders.
- Never click on the links/attachments sent by unknown senders.








