

Rewterz Threat Alert – Spear-Phishing Campaigns Deliver the BalkanRAT
December 4, 2019
Rewterz Threat Advisory – ICS: Moxa AWK-3121 Multiple Vulnerabilities
December 5, 2019
Rewterz Threat Alert – Spear-Phishing Campaigns Deliver the BalkanRAT
December 4, 2019
Rewterz Threat Advisory – ICS: Moxa AWK-3121 Multiple Vulnerabilities
December 5, 2019Severity
High
Analysis Summary
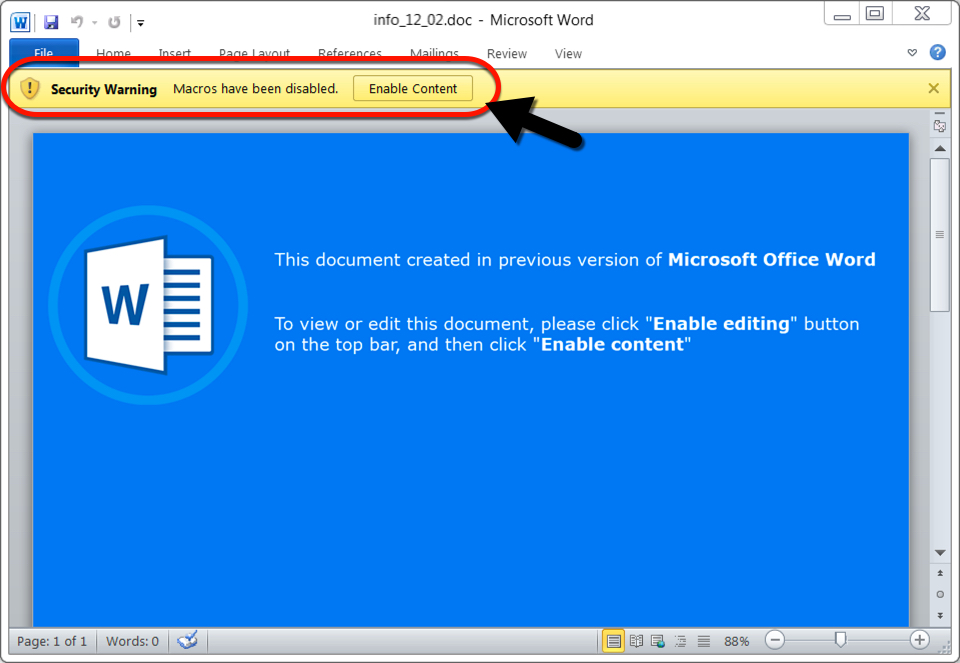
A recent Ursnif malspam campaign is seen as spoofing replies to emails and that includes Dridex as its follow-up malware. The campaign follows the typical pattern of Ursnif infection in which victims are asked to open a zip attachment containing Word documents with malicious macros. The document is password-protected and the password for the zip attachment is usually ‘777.’ It’s designed to infect a vulnerable windows host. Both Ursnif and Dridex stay persistent through the Windows registry. Ursnif copies itself and deletes the original version and Dridex remains persistent through DLL files. Enabling macros on the Word document dropped a script file in the C:\Windows\Temp directory, and the script file retrieved the initial Windows executable (EXE) file for Ursnif.
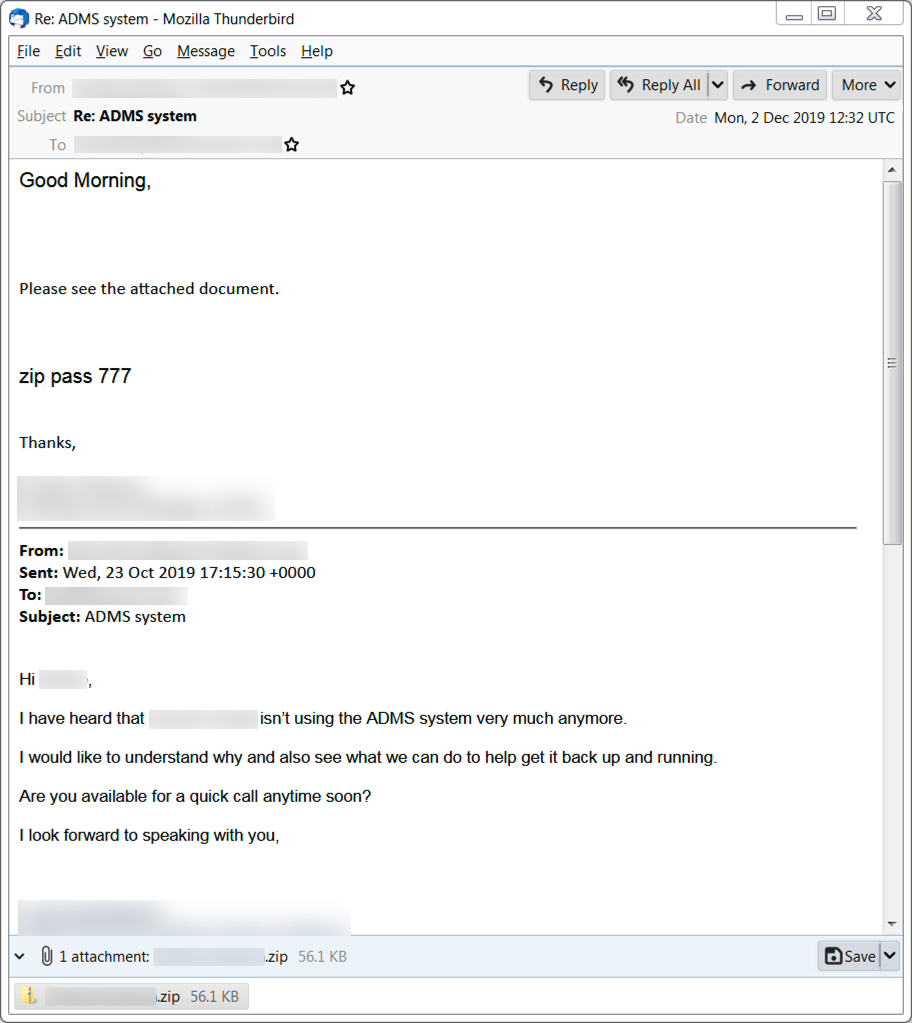
Traffic generated by Ursnif infections follows relatively consistent patterns. During these type of Ursnif infections, we often find follow-up malware retrieved by the Ursnif-infected host. In this case, it was Dridex. Dridex, a banking trojan, also known as Bugat and Cridex is a form of malware that specializes in stealing bank credentials via a system that utilizes macros from Microsoft Word.Ursnif Trojan (aka Dreambot, Gozi, and ISFB) is an information stealing trojan.
Impact
- Credential Theft
- Information Theft
- Theft of banking information
- Financial loss
Indicators of Compromise
Domain Name
- ragenommad[.]com
- nxbpierrecjf[.]com
- jyomacktom[.]top
MD5
- 12fb72db3943cc888cf36f7dc85fcb17
- b1a628273a05756c75b2068940260f3c
- 2e3877ae85fc2ddf81be959ba82d4a2b
- d608c31c16d273efce98c2f99c45f858
- f104cf6c2f4816c23b017b6d3a541e87
SHA-256
- 896fe4ae5367929ba7a48221f95d52d7795f614958c4cc1c4c7beeca4cc6b92a
- 4dcb69610bd18e00449dccb8a31f13e84fc348a242fe98cd2b4681040453fe72
- 52acd832d2036fc326743e63b2a50615be9a6e04d0b4f06e0e8d0e681bf78c9f
- 57d7f95629d7c1e0025043dc05ff1c859bb79a1616a7c4296a6ec23b27ee49cd
- d329921115fa57c30ba54e8b697658839918ac2e915c0274f2dc9028f7b9db88
Source IP
- 194.61.1[.]178
- 109.196.164[.]8
- 77.93.211[.]211
- 188.120.241[.]200
URL
- http[:]//zontcentrum[.]ru/wp-content/uploads/2019/11/unovarios.rar
- http[:]//ragenommad[.]com/edgron/siloft.php?l=utowen4.cab
Remediation
- Block the threat indicators at their respective controls.
- Do not download files attached in untrusted emails.
- Do not enable macros for untrusted files.
- Do not visit untrusted links given in untrusted emails.








