

Rewterz Threat Alert – FIN7 BOOSTWRITE’s Lost Twin exposes sensitive information
December 27, 2019
Rewterz Threat Advisory – Google Chrome Affected By Magellan 2.0 Flaws
December 30, 2019
Rewterz Threat Alert – FIN7 BOOSTWRITE’s Lost Twin exposes sensitive information
December 27, 2019
Rewterz Threat Advisory – Google Chrome Affected By Magellan 2.0 Flaws
December 30, 2019Severity
High
Analysis Summary
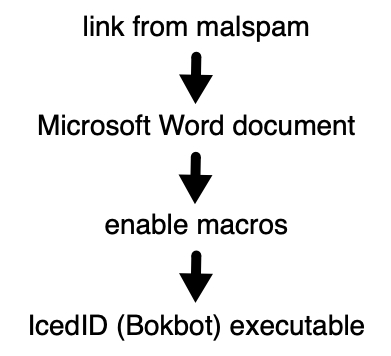
A new malspam campaign was found distributing IcedID earlier this week. The malspam pushes different Word docs from the same links, which contain IcedID, executed when a user enables content or macros for these files. Below is the infection flow for IcedID.
Below are two different samples of word documents analyzed by security researchers. The first Word document had a template that was mostly red (maybe reddish-orange). My second sample had a different template that was mostly blue.
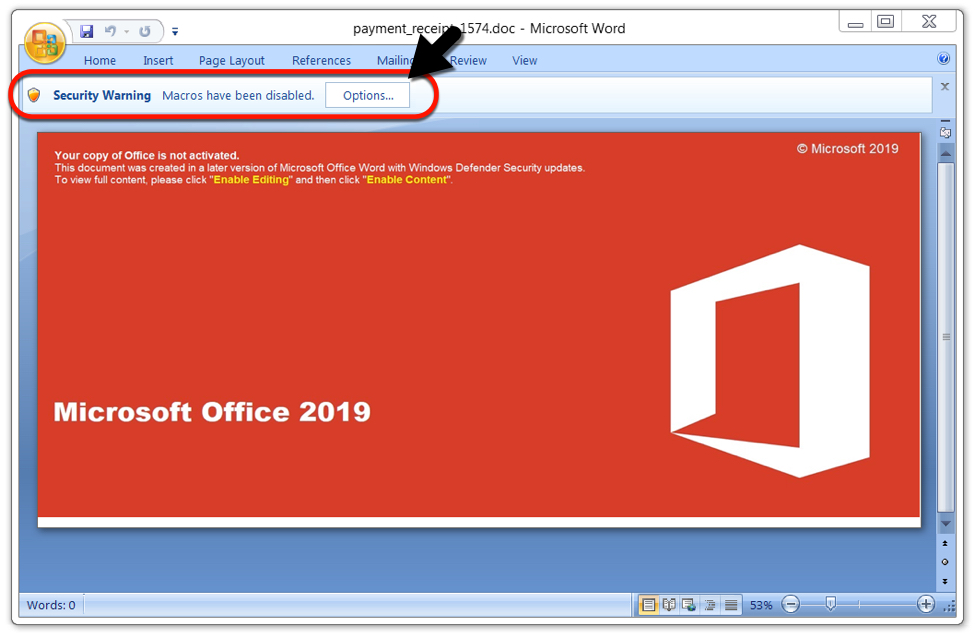
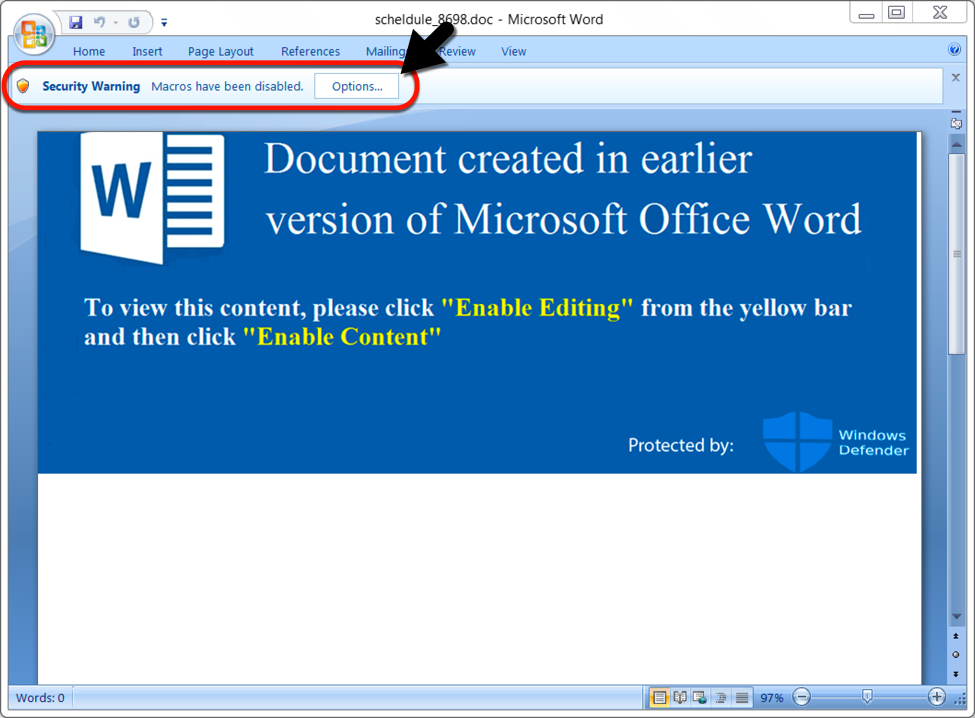
As opposed to earlier samples of IcedID, this particular infection contained no Trickbot. Infected Windows hosts showed the same type of artifacts and behavior associated with IcedID in recent months.
Impact
- Credential Theft
- Financial Loss
Indicators of Compromise
Domain Name
- mexicanfoodinmiami[.]pro
- brekatrinado[.]red
- exceptionalsanta[.]pro
- malayanfoodinmiami[.]pro
- fmjstorage[.]com
- arkanacarszoom[.]pro
- russianfoodinmiami[.]pro
- hanserefelektrik[.]com
- www[.]ticfootball[.]com
- www[.]ecowis[.]com
MD5
- 576975ee9ee9dc00eaf5c49ed9787e44
- 32cfa432c1bf621b0d7a7d2c66a91691
- 8df8d80a3b2b2b2df4359bc29e43b6b0
- bcbc51e4a4a1e2d2a8c558171c8192e9
SHA-256
- 240f62792a5874857d4f9d1663a97deb1eefd38f90c87eef76220d33c8440697
- b0430c4b64948d1fbb05ecbd7e5fc9afb068463e98718ddf01a13ddf4b4f4891
- dcadc8a97beba4bee4608739d8efc68da37c9b7035302585eb24890a5b826755
- 79723cbc2234e26aae3111b8c7b6711da68a46d01e5808598a1492e49c331f60
Source IP
- 193[.]36.60[.]3
- 162[.]241.173[.]131
- 107[.]180.41[.]89
- 162[.]241.216[.]20
- 188[.]127.227[.]76
- 95[.]217.99[.]22
URL
- http[:]//hanserefelektrik.com/wp-includes/js/mediaelement/renderers/1223/payment_receipt_1574[.]doc
- http[:]//www.ecowis[.]com/liteprjpohereo[.]exe
- http[:]//www[.]ticfootball[.]com/wp-content/uploads/2019/09/1223/scheldule_8698[.]doc
- https[:]//fmjstorage[.]com/LTCOB[.]KET
Remediation
- Block the threat indicators at their respective controls.
- Do not click on links received from untrusted email addresses.
- Do not enable macros for word documents downloaded unintentionally via links in emails from unknown sources.








