

Rewterz Threat Alert – Python RAT uses COVID-19 lures to target public and private sectors
April 21, 2020
Rewterz Threat Alert – COVID-19 Phishing Email Campaign
April 21, 2020
Rewterz Threat Alert – Python RAT uses COVID-19 lures to target public and private sectors
April 21, 2020
Rewterz Threat Alert – COVID-19 Phishing Email Campaign
April 21, 2020Severity
Medium
Analysis Summary
A new mailspam campaign is targeting multiple industries across Italy with attachments ultimately delivering the URSNIF malware. The variant used in the campaign against Italian organizations contains some important “upgrades” compared with other samples of the Ursnif malware family and a significant evolution of the attack chain. First of all, the dropper uses Excel 4.0 macros (XLM macros) in the attempt to make it hard the detection by AVs, then it uses two different C2, one of them is only used for the registration of the victim machine identified by a UUID.
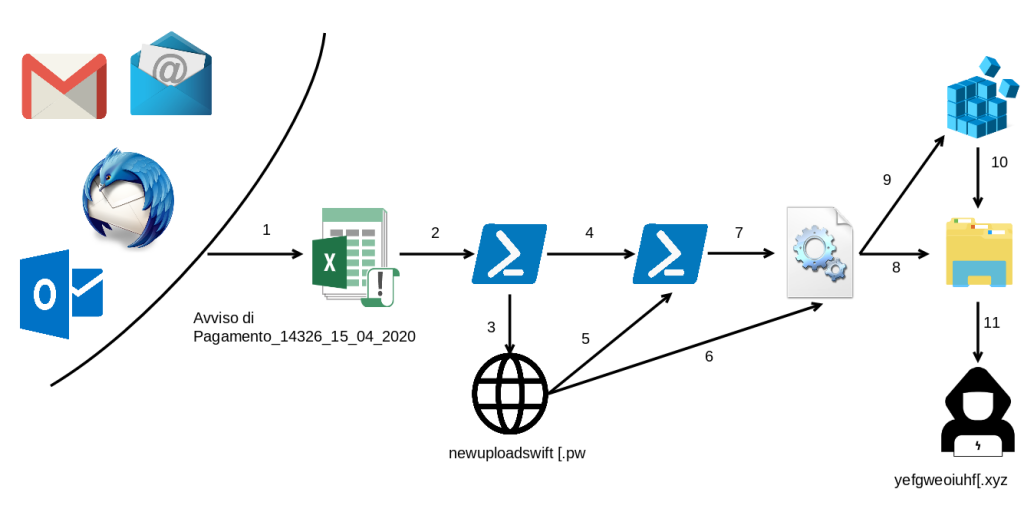
Impact
- Information theft
- Exposure of sensitive data
Indicators of Compromise
MD5
- a2ab06deeee2279099a3138c36901d92
- bae2447cc4085dc4bbadc7d6e7fb2c11
SHA-256
- 5f9da8134eece8b25f6d4da2815d49cc1ea7a5e9d2b18cec549a1ee47010c394
- e32c592819d825851bae84a33bf5fa1a26e0a57a14c0e4b8c3e845c1117998a0
SHA1
- d59a7506323019567a4f9cac0066da6c7d585d0c
- 8e29984517c2790c79c8ec33f575f46af0d95e38
URL
- https[:]//yefgweoiuhf[.]xyz/
Remediation
- Block all threat indicators at your respective controls.
- Always be suspicious about emails sent by unknown senders.
- Never click on the links/attachments sent by unknown senders.








