

Rewterz Threat Alert – Android Trojan Delivered via Chat Application
December 26, 2019
Rewterz Threat Alert – Non Encryption of Linux Folders in Ryuk Ransomware
December 27, 2019
Rewterz Threat Alert – Android Trojan Delivered via Chat Application
December 26, 2019
Rewterz Threat Alert – Non Encryption of Linux Folders in Ryuk Ransomware
December 27, 2019Severity
Medium
Analysis Summary
Malicious spam campaigns delivering malware in disk image file formats, .ISO being the most used in this case. Among the most popular threats delivered this way are remote access tools (NanoCore, Remcos) and LokiBot information stealer.
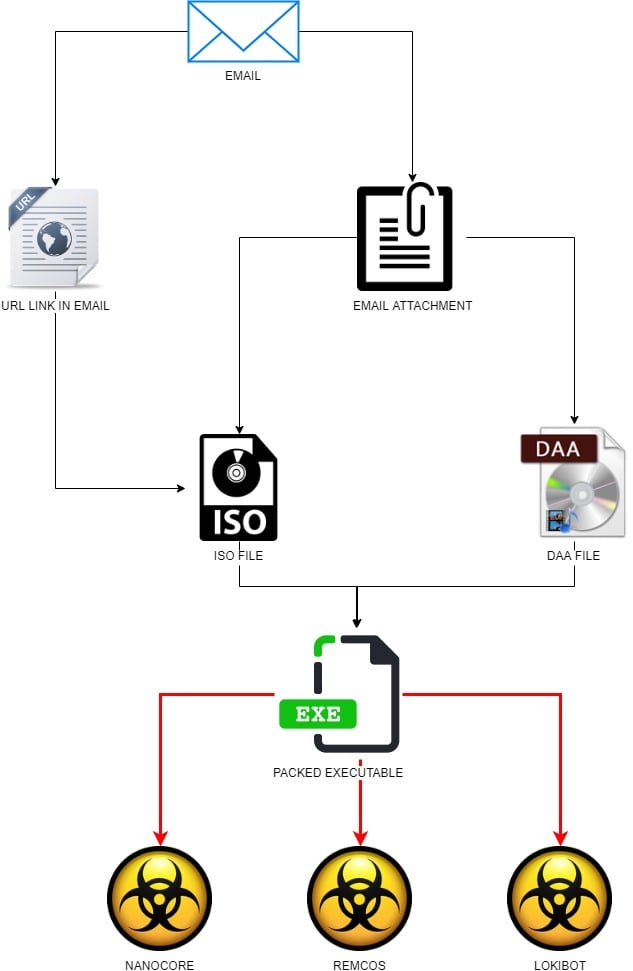
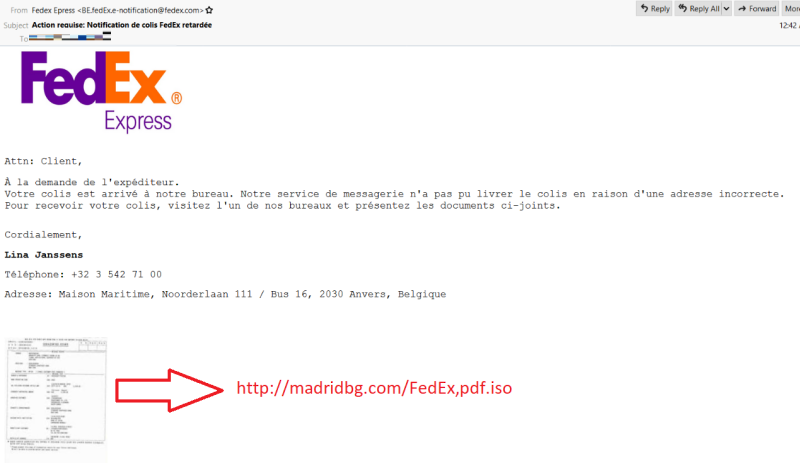
Choosing ISO to deliver malware makes sense since Windows operating system has the ability to mount this file type when double-clicked. This allows scammers to disguise the threat as an innocent file. In a recent campaign, threat actors created a fake FedEx shipment email message to trick recipients into downloading a malicious ISO that included an executable.
Impact
- Exposure of sensitive information
- Credential theft
Remediation
- Block all threat indicators at your respective controls.
- Always be suspicious about emails sent by unknown senders.
- Never click on the links/attachments sent by unknown senders.
- Always look for legitimate URL of the website you land in, when you click on the link via email.








