

Rewterz Threat Alert – Buhtrap Group Recent Activity
July 17, 2019
Rewterz Threat Alert – Sea Turtle Adopts New DNS Hijacking Techniques
July 18, 2019
Rewterz Threat Alert – Buhtrap Group Recent Activity
July 17, 2019
Rewterz Threat Alert – Sea Turtle Adopts New DNS Hijacking Techniques
July 18, 2019Severity
Medium
Analysis Summary
A new, fully undetected Linux backdoor implant, containing rarely seen functionalities with regards to Linux malware, targeting desktop users. The evidence shows operational similarities between this implant and Gamaredon Group.
Gamaredon Group is an alleged Russian threat group. It has been active since at least 2013, and has targeted individuals likely involved with the Ukrainian government. Gamaredon Group infects victims using malicious attachments, delivered via spear phishing techniques. The group’s implants are characterized by the employment of information stealing tools—among them being screenshot and document stealers delivered via a SFX, and made to achieve persistence through a scheduled task.
Hosting Similarities
The operators of EvilGnome use a hosting provider that has been used by Gamaredon Group for years, and continues to be used by the group.

Technical Analysis
Deployment with Makeself SFX
This implant is delivered in the form of a self-extracting archive shell script created with makeself:
“makeself.sh is a small shell script that generates a self-extractable compressed tar archive from a directory. The resulting file appears as a shell script (many of those have a .run suffix), and can be launched as is. The archive will then uncompress itself to a temporary directory and an optional arbitrary command will be executed (for example an installation script). This is pretty similar to archives generated with WinZip Self-Extractor in the Windows world.”
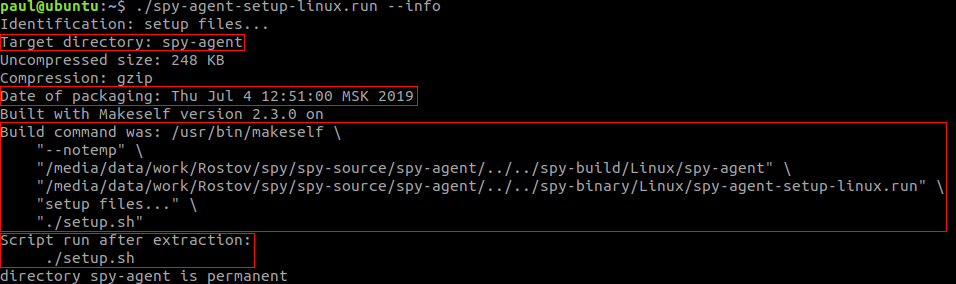
As can be observed in the illustration above, the makeself script is instructed to run ./setup.sh after unpacking.
Using makeself’s options, we are able to instruct the script to unpack itself without executing:

The archive contains four files:
- gnome-shell-ext – the spy agent executable
- gnome-shell-ext.sh – checks if gnome-shell-ext is already running and if not, executes it
- rtp.dat– configuration file for gnome-shell-ext
- setup.sh – the setup script that is run by makeself after unpacking
Impact
- Information steal
- Exposure of sensitive information
Indicators of Compromise
URLs
- clsass[.]ddns[.]net
- gamework[.]ddns[.]net
- kotl[.]space
- rnbo-ua[.]ddns[.]net
- workan[.]ddns[.]net
Malware Hash (MD5/SHA1/SH256)
- 044e14f9a6766d116646914829282fe78784b55d031224a99b1ca68eb099bf30
- 49d967385e4e3a059fab5d6e5a844f7195ab9cf535ce075f5ba296d51036b710
- 6e4989a1b4625042e66c2e92500238ca9b2ed7f6d34d51ecb0c6f9c183e59e96
- 7ffab36b2fa68d0708c82f01a70c8d10614ca742d838b69007f5104337a4b869
- 82b69954410c83315dfe769eed4b6cfc7d11f0f62e26ff546542e35dcd7106b7
- 88b4d7f38d475aaaae4a72b402e65b6dc32cad6411cddff35e025826da08a5f4
- 8a644b1c8173745bf5909c4b53b39a66bd6a45673a2e10ae88b6990a96a77348
- 909a9e67517a49ac10e8859c2efa5a613166f2a36ec8761905e4b5a8c3a90f57
- a21acbe7ee77c721f1adc76e7a7799c936e74348d32b4c38f3bf6357ed7e8032
- a6c5709649eb2d053af82e70aa12b1fc2a8938959066c6bdfa0b92cd0db1fc85
- bfc8f56c28efa2a07844c6f9ff33556de0baf052b5ced421c9bb04a94f3ded0f
- c58168ca5ee709da20355ccd447f760d3fb6b63f372bd4344e0c824cfbc55ff1
- cec6e01b1e3097f8a80b892a091446230a7460292136d53ff12639bc0db82241
- ded4ea9f386226d93f2b5cd2af253bb8e33ca69cb130f5facba7545f142b6e1e
Remediation
It is recommended for the users to check “~/.cache/gnome-software/gnome-shell-extensions” directory for the “gnome-shell-ext” executable.








