

Rewterz Threat Alert – FTCODE Ransomware — New Version Harvests Saved Credentials
January 21, 2020
Rewterz Threat Advisory – ICS: Honeywell Maxpro VMS & NVR
January 22, 2020
Rewterz Threat Alert – FTCODE Ransomware — New Version Harvests Saved Credentials
January 21, 2020
Rewterz Threat Advisory – ICS: Honeywell Maxpro VMS & NVR
January 22, 2020Severity
High
Analysis Summary
The Emotet malware has started using spam templates of sextortion and ransomware campaigns. At first, it used an extortion demand from a “pretend Hacker” who states that they hacked the recipient’s computer and stole their data. Later, operators at Emotet sent out sextortion emails that stated that an attacker recorded video of the recipient while on adult sites. The attackers demanded $500 to $3000 extortion payment and threatened to spread the videos, which earned them $50,000 in a week.
The latest campaign threatens to sell victim’s data on the black market, and uses “INF Jan 17 20.doc for [Name]” or “For [Name]” for the email subjects. Few samples are given below.
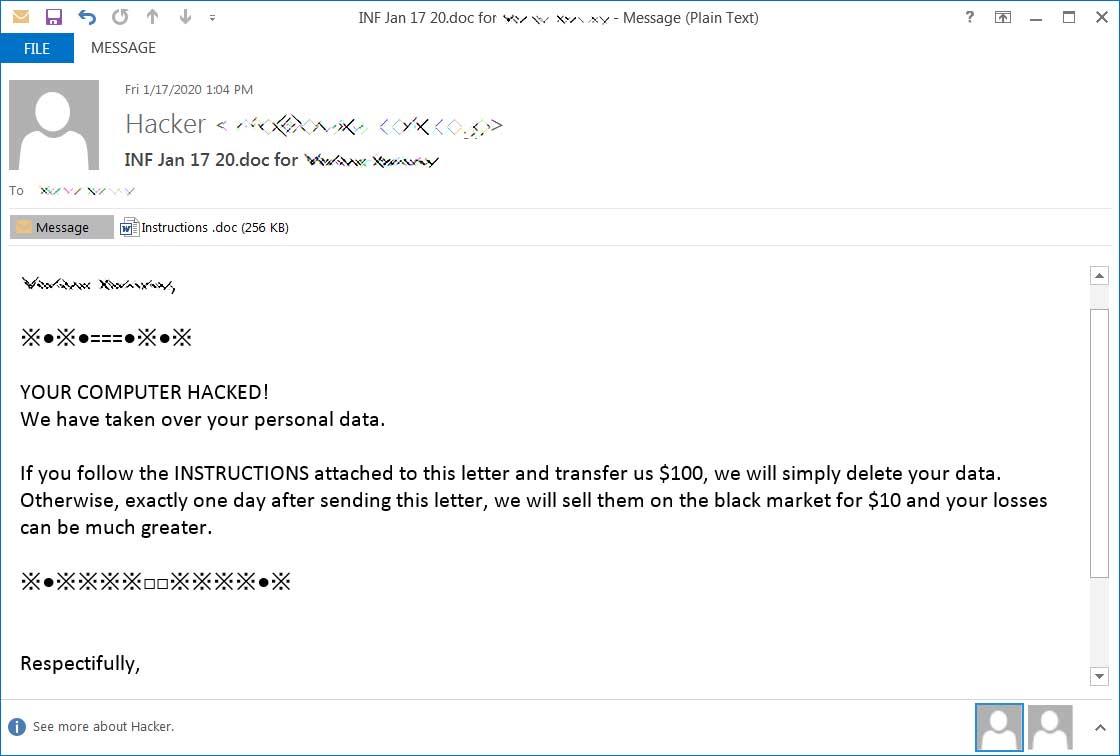
Another one of these emails reads as follows:
“YOUR COMPUTER HACKED!
We have taken over your personal data and financial data.If you follow the instructions attached to this letter and transfer us $ 50, we will simply delete your data.
Otherwise, exactly one day after sending this letter, we will sell them on the black market for $ 10 and your losses can be much greater.Nothing personal is just a business.
Have a nice day. I hope for your cooperation”
When the target opens the document, it opens a word template demanding the user to ‘enable content’.
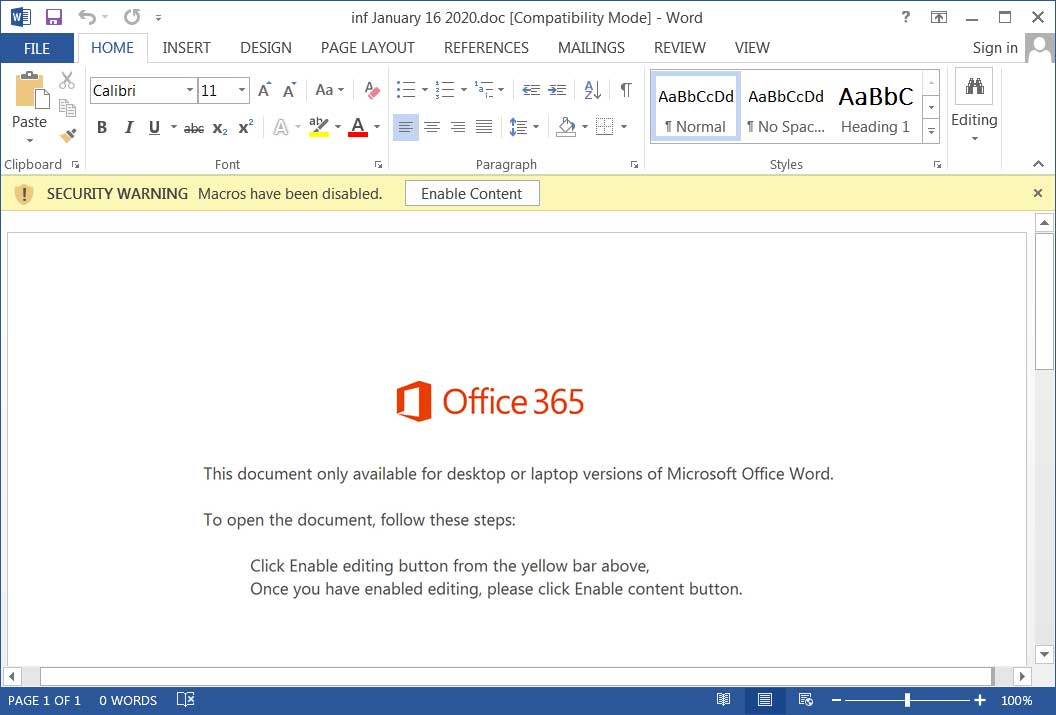
Once the document is opened, a PowerShell command will be executed that downloads and installs the Emotet Trojan on the computer, followed by installation of TrickBot information-stealing Trojan, which will begin to steal your login credentials, sensitive files, browser history, and more.
On high-value networks, TrickBot also fetches RYUK ransomware that will open a reverse shell back to them so that the Ryuk operators can encrypt the entire network.
Impact
- Financial scam
- Credential Theft
- Information Theft
- Files encryption
- Network-wide infection
Indicators of Compromise
Domain Name
- kyowa[.]cc
- manorviews[.]co[.]nz
- oniongames[.]jp
- kimtgparish[.]org
- friendzonecafe[.]com
- taobaoraku[.]com
- zhangpalace[.]com
- jayracing[.]com
- vikisa[.]com
- iihttanzania[.]com
- blulinknetwork[.]com
- vanezas[.]com
- www[.]jalanuang[.]com
- kameldigital[.]com
- orlandohoppers[.]com
- thebenefitshubtraining[.]com
- shopaletta[.]com
- expresodeportivo[.]com
Hostname
- www[.]yougeniusads[.]com
MD5
- c82f51b317ab2661f00126d435f6814b
SHA-256
- b5347868ebc65f0e1df451068e08db6d161a372c05bb760fd6d004332620aa5c
Source IP
- 192[.]169[.]231[.]214
Remediation
- Block the threat indicators at their respective controls.
- Do not respond to such emails and mark as spam for future filtration.
- Do not download files attached in emails coming from untrusted sources.
- Do not enable macros for untrusted files.








