

Rewterz Threat Advisory – ManageEngine Application Manager Execute Program Action feature Privilege Escalation
August 13, 2019
Rewterz Threat Alert – Elusive Ransomware Sodinokibi
August 13, 2019
Rewterz Threat Advisory – ManageEngine Application Manager Execute Program Action feature Privilege Escalation
August 13, 2019
Rewterz Threat Alert – Elusive Ransomware Sodinokibi
August 13, 2019Severity
Medium
Analysis Summary
A phishing campaign targeting specific individuals, using DocuSign-themed lures and leveraging a public cloud storage service to host landing pages. The targeted users are from a variety of companies, but there appears to be no industry-specific targeting. The landing pages contain obfuscated JavaScript code and draw resources from multiple sites, some of which have TLS certificates associated with the email address contained in the list.
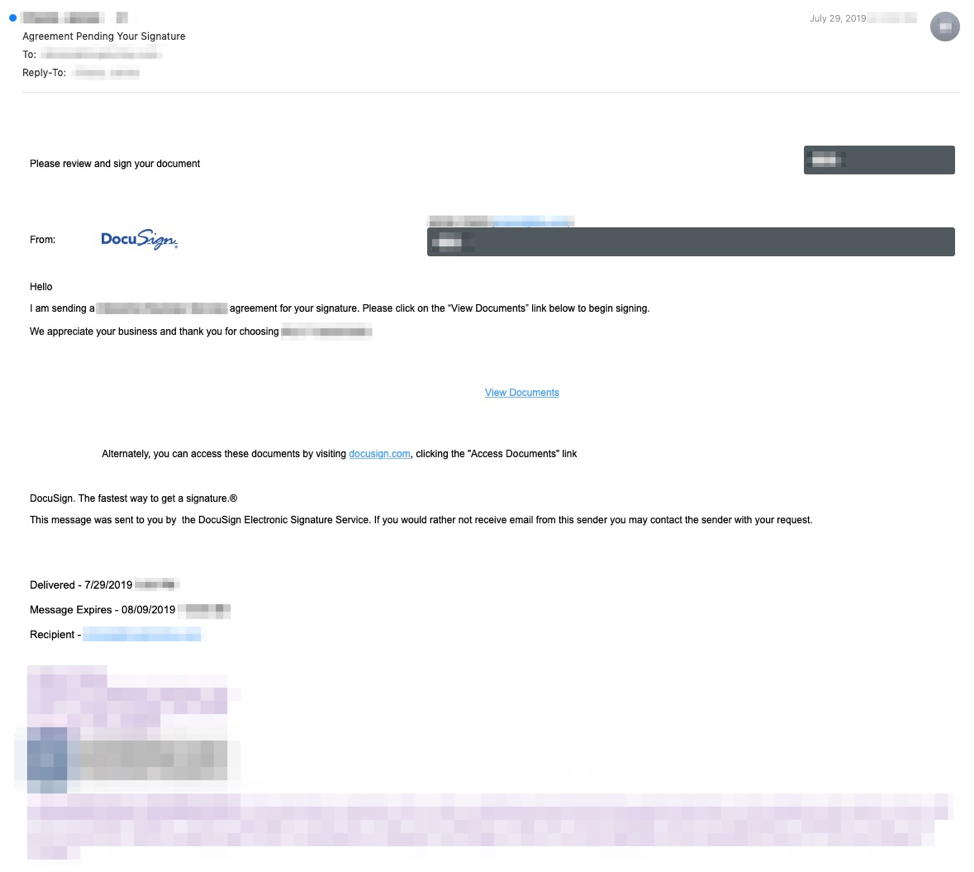
While the landing page for the credential phish also convincingly resembles DocuSign in branding and overall format, it is actually a phishing template that has been commonly used over the past few years:
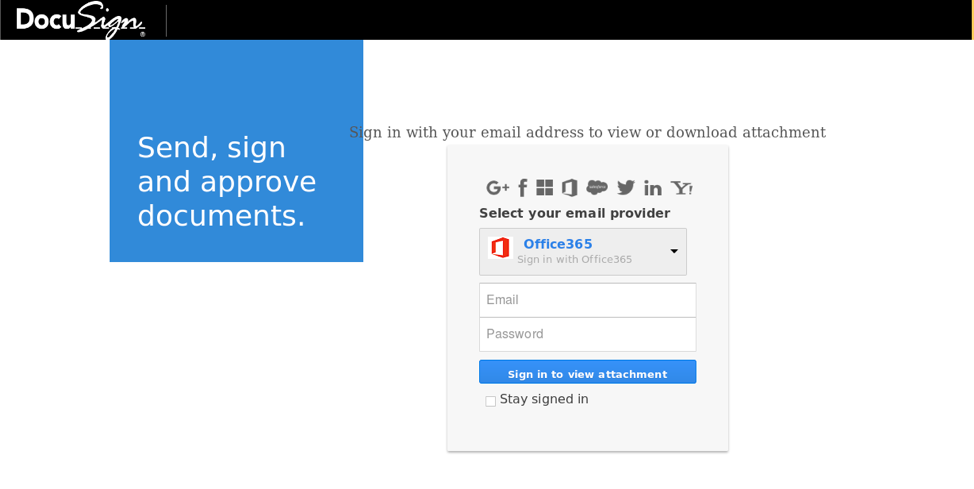
Impact
Credential theft
Indicators of Compromise
IP(s) / Hostname(s)
- 185[.]255[.]79[.]118
- 194[.]58[.]112[.]174
URLs
- postmasterpledge[.]ru
- dataanarchyofsons[.]site
- whistleobohemian[.]info
- 300spartans[.]dancelikejoseph[.]xyz
- xplicate[.]dancelikejoseph[.]info
- dancelikejoseph[.]site
Remediation
- Block all threat indicators at your respective controls.
- Always be suspicious about emails sent by unknown senders.
- Never click on the link/attachments sent by unknown senders.








