

Rewterz Threat Alert – PayPal Phishing Attacks
December 23, 2019
Rewterz Threat Alert – Maze ransomware – IOCs
December 23, 2019
Rewterz Threat Alert – PayPal Phishing Attacks
December 23, 2019
Rewterz Threat Alert – Maze ransomware – IOCs
December 23, 2019Severity
High
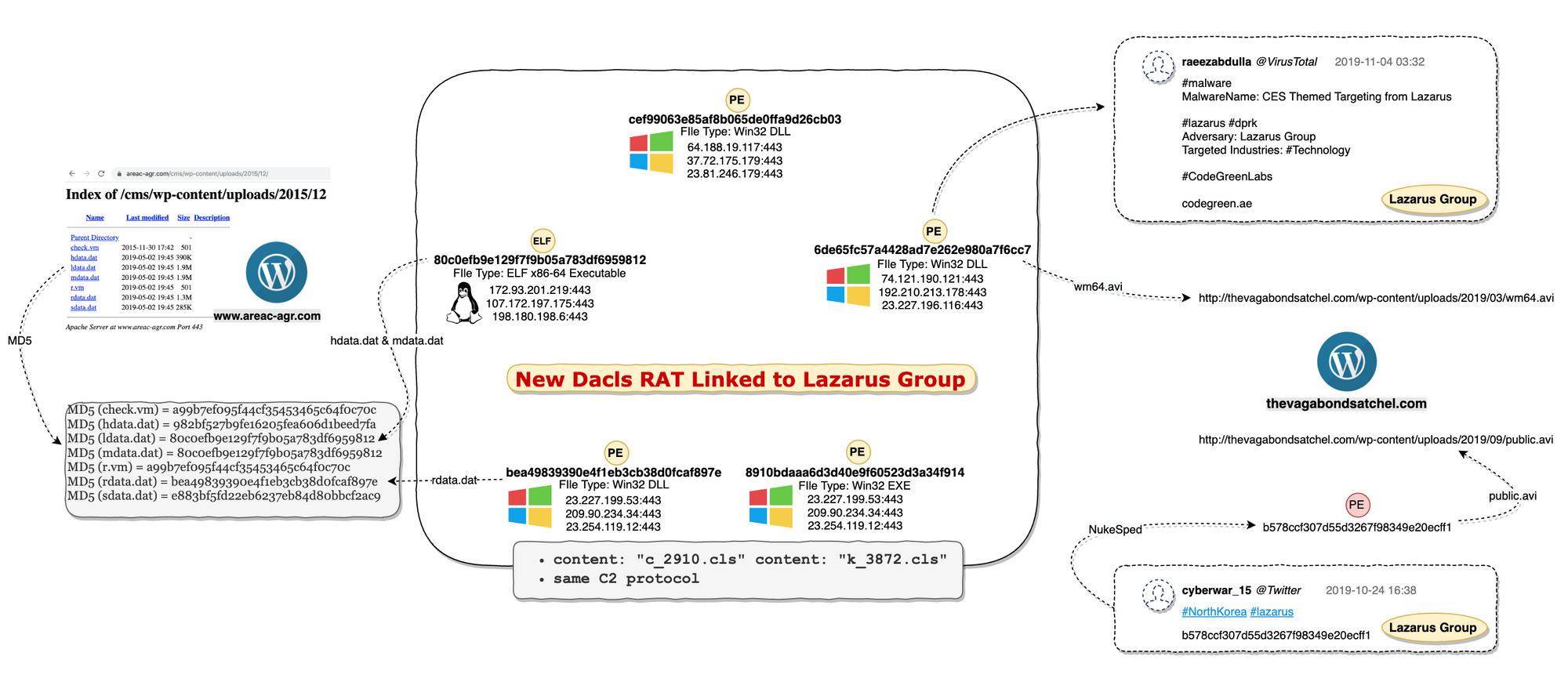
Analysis Summary
Dacls is a new type of remote-control software targeting both Windows and Linux environment. Its functions are modular, the C2 protocol uses TLS and RC4 double-layer encryption, the configuration file uses AES encryption and supports C2 instruction dynamic update. The Win32.Dacls plug-in module is dynamically loaded through a remote URL, and the Linux version of the plug-in is compiled directly in the Bot program.
Impact
Exposure of sensitive information
Indicators of Compromise
IP
- 23[.]81[.]246[.]179
- 23[.]254[.]119[.]12
- 23[.]227[.]196[.]116
- 37[.]72[.]175[.]179
- 23[.]227[.]199[.]53
- 107[.]172[.]197[.]175
- 172[.]93[.]201[.]219
- 64[.]188[.]19[.]117
- 74[.]121[.]190[.]121
- 192[.]210[.]213[.]178
- 209[.]90[.]234[.]34
- 198[.]180[.]198[.]6
MD5
- 6de65fc57a4428ad7e262e980a7f6cc7
- 80c0efb9e129f7f9b05a783df6959812
- 982bf527b9fe16205fea606d1beed7fa
- 8910bdaaa6d3d40e9f60523d3a34f914
- a99b7ef095f44cf35453465c64f0c70c
- bea49839390e4f1eb3cb38d0fcaf897e
- cef99063e85af8b065de0ffa9d26cb03
- e883bf5fd22eb6237eb84d80bbcf2ac9
URL
- http[:]//www[.]areac-agr[.]com/cms/wp-content/uploads/2015/12/check[.]vm
- http[:]//www[.]areac-agr[.]com/cms/wp-content/uploads/2015/12/hdata[.]dat
- http[:]//www[.]areac-agr[.]com/cms/wp-content/uploads/2015/12/ldata[.]dat
- http[:]//www[.]areac-agr[.]com/cms/wp-content/uploads/2015/12/mdata[.]dat
- http[:]//www[.]areac-agr[.]com/cms/wp-content/uploads/2015/12/r[.]vm
- http[:]//www[.]areac-agr[.]com/cms/wp-content/uploads/2015/12/rdata[.]dat
- http[:]//www[.]areac-agr[.]com/cms/wp-content/uploads/2015/12/sdata[.]dat
Remediation
- Block all threat indicators at your respective controls.
- Always be suspicious about emails sent by unknown senders.
- Never click on the links/attachments sent by unknown senders.








