Severity
High
Analysis Summary
A new spate of Jackpotting attacks have been on the rise all over the world where the ATM machines are being injected a piece of malware called “Cutlet Maker” that is designed to make ATMs eject all of the money inside them. In case of a successful attack the term is defined as “Jackpot” which means the machine will eject out all the available cash in the ATM machine.
Jackpotting is a technique where cybercriminals use malware or a piece of hardware to trick an ATM into ejecting all of its cash, no stolen credit card required. Hackers typically install the malware onto an ATM by physically opening a panel on the machine to reveal a USB port.
Recently the attack region of these attacks have U.S., Latin America, and Southeast Asia, and the issue impacts banks and ATM manufacturers across the financial industry.
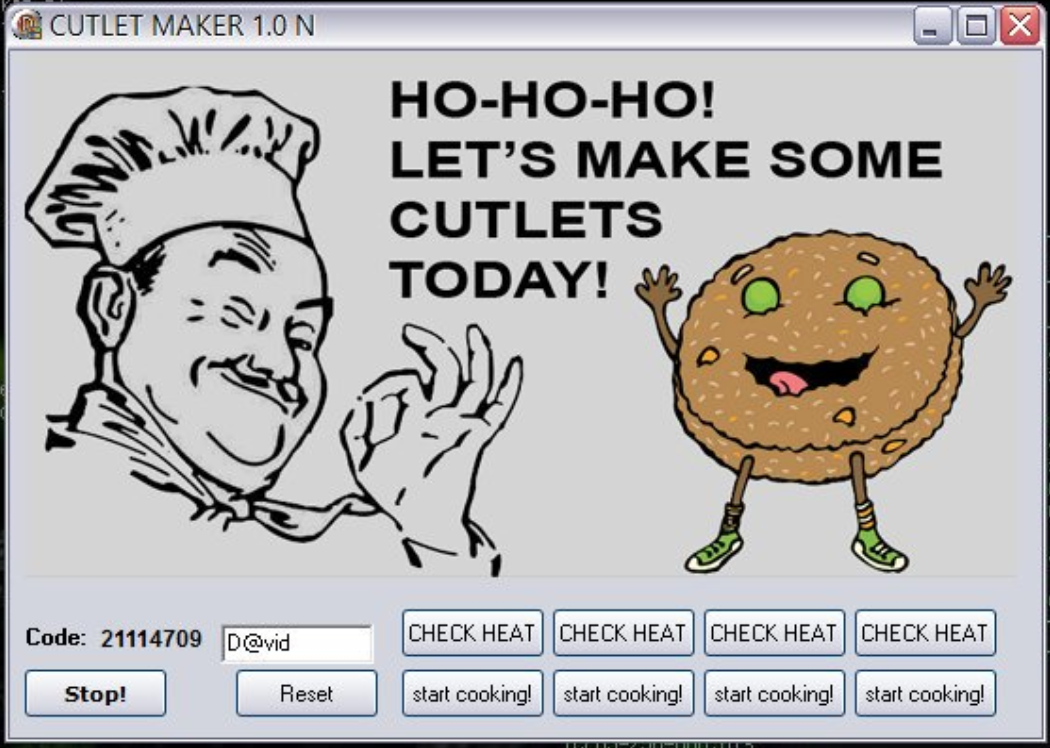
“Ho-ho-ho! Let’s make some cutlets today!” Cutlet Maker’s control panel reads, alongside cartoon images of a chef and a cheering piece of meat. In an apparent Russian play-on-words, a cutlet not only means a cut of meat, but a bundle of cash, too.
Diebold Nixdorf’s Wincor 2000xe model of ATM was targeted several times in the German financial market and it can targeted somewhere in the region too.
Jackpotting attacks are not specific to any specific vendor or specific model of the ATM machines. Any machine with any model number can be targeted by it.
Impact
Financial loss
Remediation
- Enabling device control mechanisms to restrict any sort of unauthorized devices to the ATM.
- Implement strict default-deny policies preventing any unauthorized software from running on the ATM.

