

Rewterz Threat Alert – Malspam NanoCore RAT Malware
April 23, 2020
Rewterz Threat Advisory – CVE-2020-1967 – OpenSSL Segmentation fault in SSL_check_chain Vulnerability
April 23, 2020
Rewterz Threat Alert – Malspam NanoCore RAT Malware
April 23, 2020
Rewterz Threat Advisory – CVE-2020-1967 – OpenSSL Segmentation fault in SSL_check_chain Vulnerability
April 23, 2020Severity
High
Analysis Summary
A new phishing campaign is underway that targets a company’s employees with fake customer complaints that install a new backdoor used to compromise a network. Many corporate employees have been receiving fake emails pretending to be from their company’s “Corporate Lawyer”. Subjects like “Re: customer complaint in [insert company name]” or “Re: customer complaint for [recipient name]” are being used to trigger employees. They state that the recipient’s employer has received a customer complaint about them. Due to this, the employee will be fined and have the amount deducted from their salary. Have a look at the sample below.
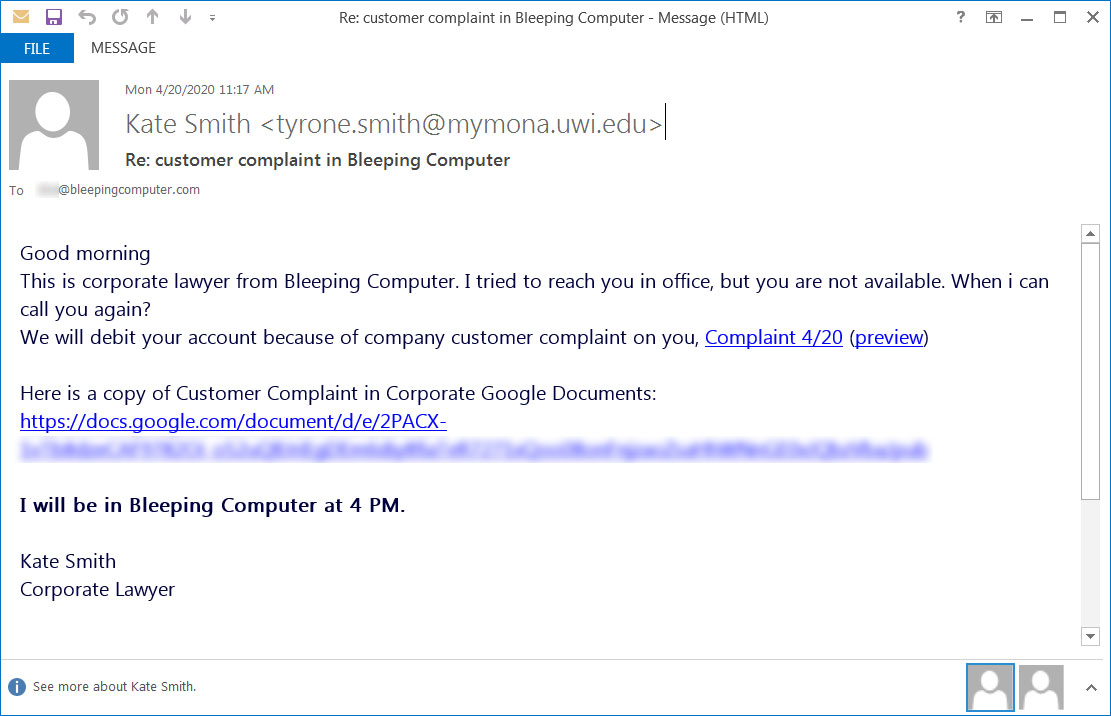
When a user visits this google docs link, they will see a stylized Google Docs document looking like a customer complaint with information on how to download it.
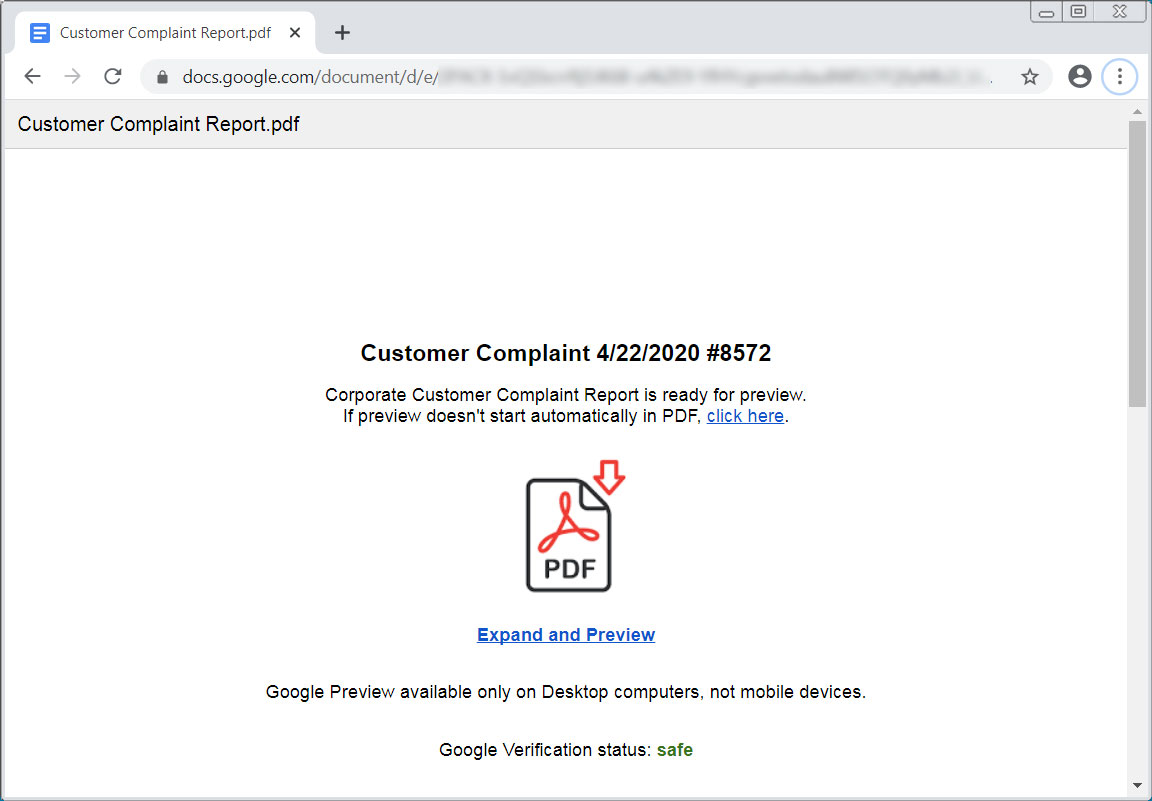
When a user clicks on the “Expand and Preview” link, a file named Prevew.PDF.exe will be downloaded. This file that looks like a PDF is not its true file type. This is a new executable backdoor called ‘bazaloader’ based on the domain used by its command and control server. When a user tries to view the PDF on Google Docs, they will be prompted to “Expand and Preview” it, which will cause a file to be downloaded.
When executed, the malware will inject itself into the legitimate C:\Windows\system32\svchost.exe and then proceed to connect to a remote server command & control server where it will send data and receive further commands or payloads. Researchers suspect that this backdoor is used for downloading Cobalt Strike. Once Cobalt Strike is deployed, the attackers gain full access to the victim’s computer and can use it to compromise the rest of the network to install ransomware or steal data to be used for extortion.
Impact
- Information Theft
- Full system compromise
- Network wide compromise
Indicators of Compromise
Filename
Prevew[.]PDF[.]exe
MD5
fd18f895de2806d7bfe6fcbd189e4bb9
SHA-256
1e123a6c5d65084ca6ea78a26ec4bebcfc4800642fec480d1ceeafb1cacaaa83
Remediation
- Block the threat indicators at their respective controls.
- Ensure employee awareness so that they can confirm the legitimacy of such emails before downloading an executable. As email addresses can be spoofed or compromised in BEC attacks, employees should be aware of such possibilities and must not instinctively click on such links.
- Always enable file extensions in Windows so that you can quickly identify if the file you’re downloading is not its true file type. (an exe in guise of a PDF)








