

Rewterz Threat Alert – Thanksgiving eCard Emails Distributing Malware
November 29, 2019
Rewterz Threat Alert – Nanobot Backdoor – IOC’s
December 2, 2019
Rewterz Threat Alert – Thanksgiving eCard Emails Distributing Malware
November 29, 2019
Rewterz Threat Alert – Nanobot Backdoor – IOC’s
December 2, 2019Severity
Medium
Analysis Summary
A new Windows trojan has been discovered that attempts to steal passwords stored in the Google Chrome browser. While this is nothing unique, what stands out is that the malware uses a remote MongoDB database to store the stolen passwords.
This trojan is called CStealer, and like many other info-stealing trojans, was created to target and steal login credentials that were saved in Google Chrome’s password manager.
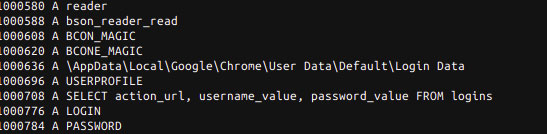
Instead of compiling the stolen passwords into a file and sending them to a C2 under the attackers control, the malware connects directly to a remote MongoDB database and uses it to store the stolen credentials.
To do this, the malware includes hardcoded MongoDB credentials and utilizes the MongoDB C Driver as a client library to connect to the database.
While this method ultimately serves its purpose of stealing passwords, it also opens the door for other attackers to gain access to the victim’s credentials.
Impact
Credential theftI
Remediation
- Always be suspicious about emails sent by unknown senders.
- Never click on the links/attachments sent by unknown senders.








