

Rewterz Threat Alert – Adwind Bypasses Microsoft ATP to Attack Utilities Industry
August 22, 2019
Rewterz Threat Advisory – CVE-2019-15295 – BitDefender Antivirus Free 2020 – Privilege Escalation to SYSTEM
August 22, 2019
Rewterz Threat Alert – Adwind Bypasses Microsoft ATP to Attack Utilities Industry
August 22, 2019
Rewterz Threat Advisory – CVE-2019-15295 – BitDefender Antivirus Free 2020 – Privilege Escalation to SYSTEM
August 22, 2019Severity
High
Analysis Summary
Advance hacker group Silence has increased their activity significantly over the past year. Victims in the financial sector are scattered across more than 30 countries and financial losses have quintupled. Started in 2016, Silence group has attracted many eye balls after initial fail over their victims, since then it has managed to steal at least $4.2 million, initially from banks in the former Soviet Union, then from victims in Europe, Latin America, Africa, and Asia.
Tools and Tactics
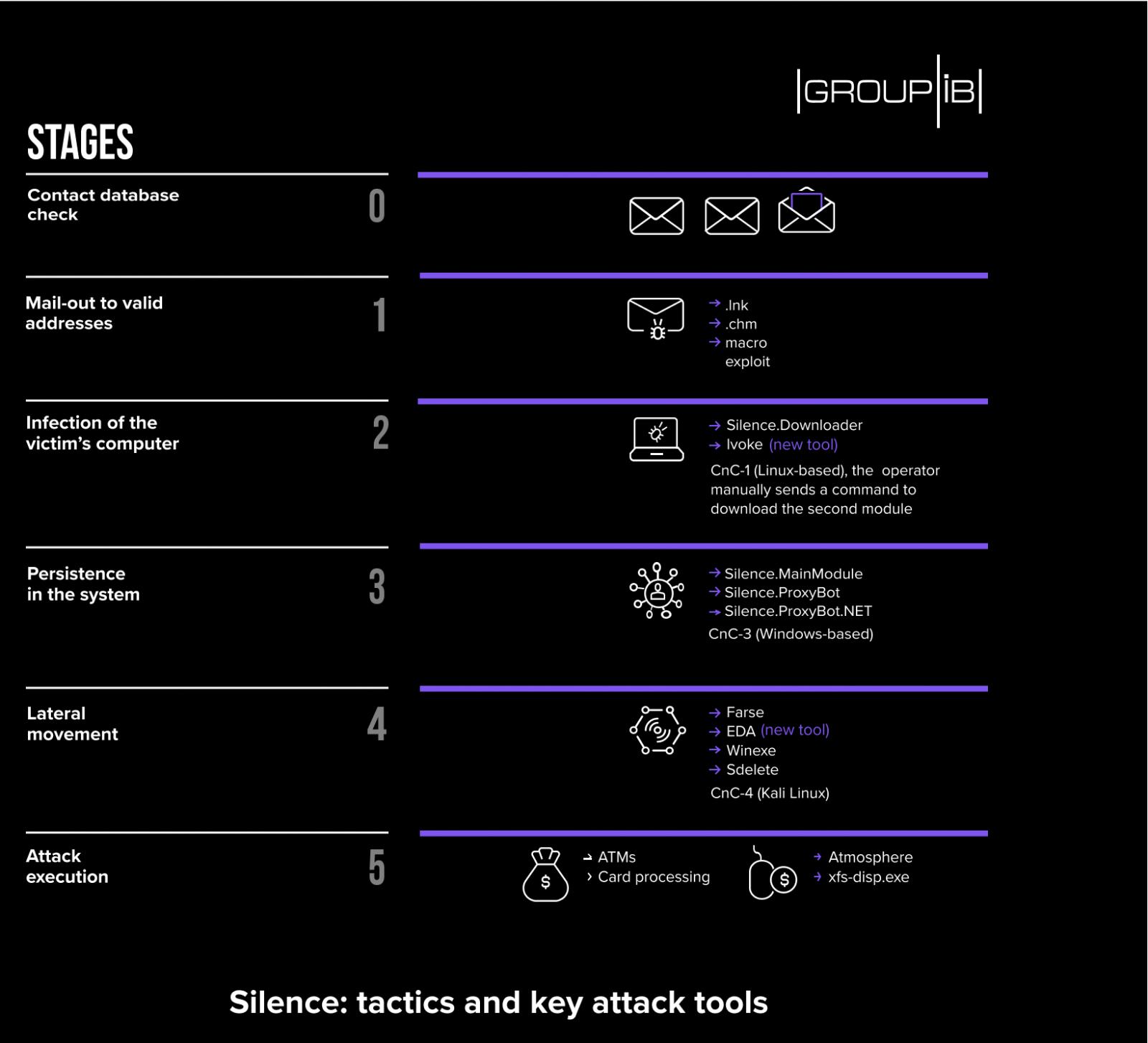
The researchers say that Silence has improved its operational security and changed its toolset to thwart detection. Apart from rewriting the first-stage module (Silence.Downloader / Truebot), the group began using a PowerShell-based fileless loader called Ivoke.
For lateral movement in the victim network, a new PowerShell agent is used, called EmpireDNSAgent (EDA) because it is based on the recently abandoned Empire framework and the dnscat2 project.
In October 2018, Silence started to send out reconnaissance emails that would help better prepare an attack. Such a message would carry no payload and pretended to be an automated reply for a failed delivery.
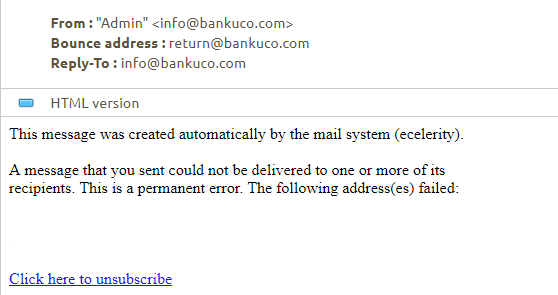
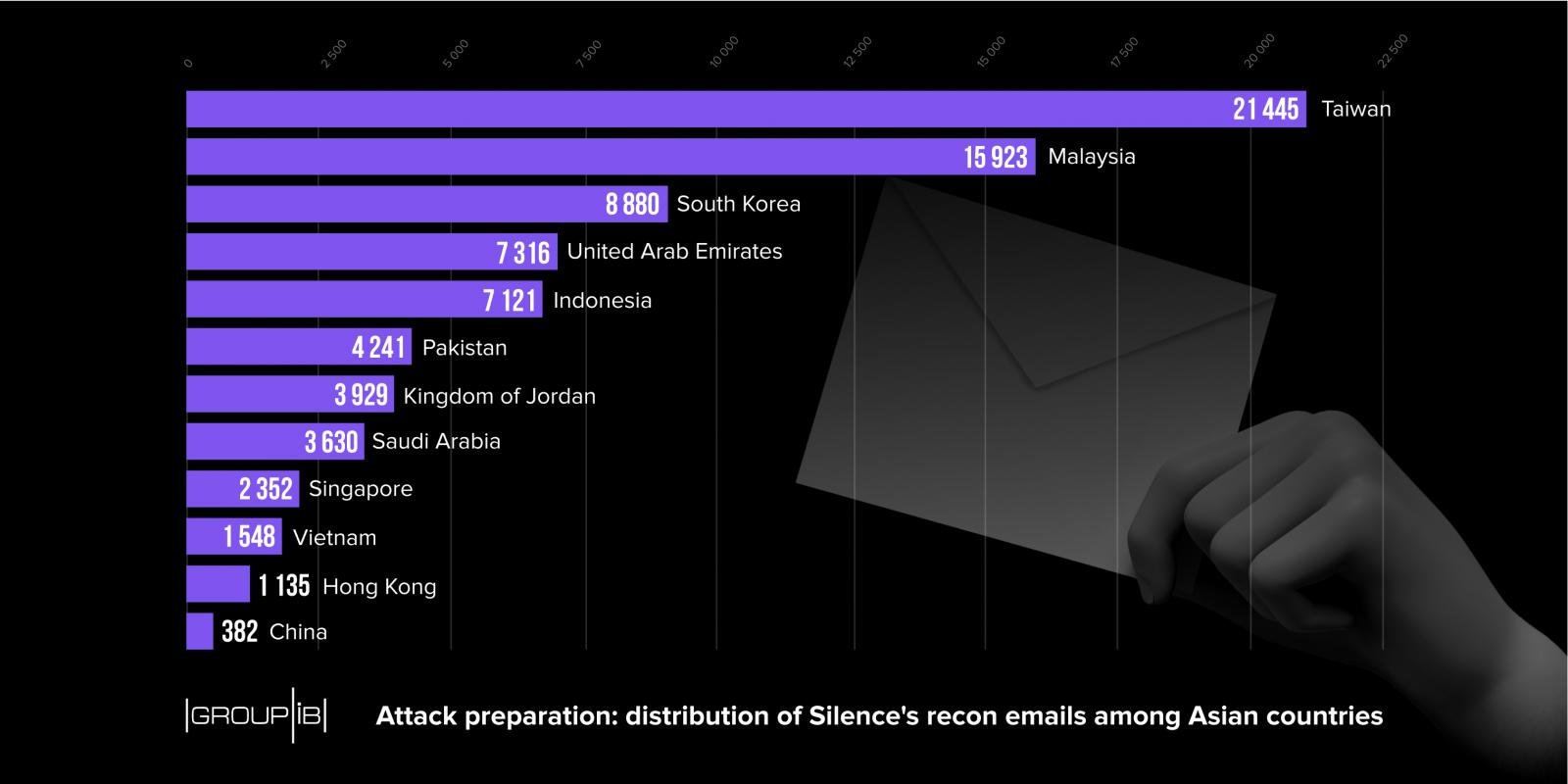
The purpose was to receive an updated list of active email addresses from the target. Silence sent out over 170,000 of these emails during three separate campaigns against victims in Asia, Europe, and post-Soviet countries.
The recon campaign on financial institutions in Europe was the smallest one, with less than 10,000 emails delivered. The focus was on British financial companies.
After validating email addresses, the threat actor moves to the next stages of the attack and starts sending out messages with a payload that downloads Silence-specific malware.
Persistence and lateral movement follow, using self-developed tools or binaries already available on the target system.
In the final stage, the attacker reaches the card processing machines and can control ATMs using its Atmosphere trojan or a program called ‘xfs-disp.exe’ to dispense cash to money mules at specific times.
Impact
Financial loss
Remediation
- Always be suspicious about emails sent by unknown senders.
- Never click on the link/ attachments sent by unknown senders.








