

Rewterz Threat Advisory – CVE-2019-13945 – ICS: Undocumented access feature in Siemens SIMATIC PLCs Code Execution Vulnerability
November 18, 2019
Rewterz Threat Alert – Buran Ransomware Infects PCs via Microsoft Excel Web Queries
November 19, 2019
Rewterz Threat Advisory – CVE-2019-13945 – ICS: Undocumented access feature in Siemens SIMATIC PLCs Code Execution Vulnerability
November 18, 2019
Rewterz Threat Alert – Buran Ransomware Infects PCs via Microsoft Excel Web Queries
November 19, 2019Severity
Medium
Analysis Summary
A New Multiplatform Backdoor targeting Linux which does not have any known connections to other threat groups.
Technical Analysis
The Linux binary is a statically linked ELF file, while the Windows binary is a dynamically linked PE file.
Both instances of this malware are practically identical in terms of overall functionality, with minor implementation differences. However, if we pay close attention to each instance we can draw some conclusions regarding the nature of the authors.
Both malware instances share the same protocol to communicate with the same CNC server. However, these instances have different delivery vectors:

Backdoor Analysis
The Windows variant of this malware does not represent a complex threat in terms of Windows malware. Conversely, the Linux variant shows more sophistication in regards to the implementation details used to replicate the same functionality.

This indicates information regarding the malware authors’ development environment preference.
The main function is not obfuscated and appears to be straightforward in logic. In the Windows variant we can see how some strings are decoded in the beginning of the function.
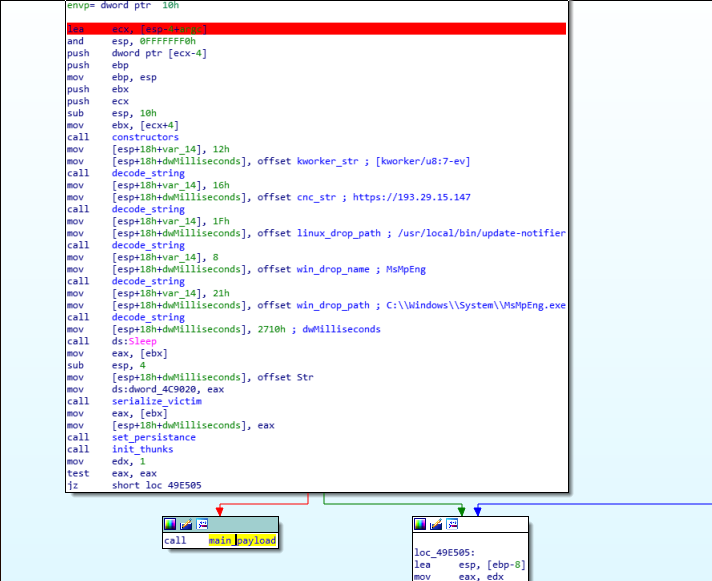
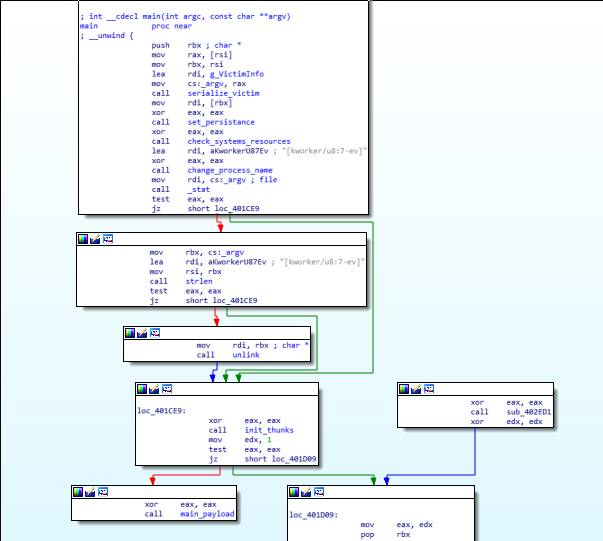
Impact
- Arbitrary execution of shell commands
- Arbitrary binary execution
Indicators of Compromise
IP
- 185[.]198[.]56[.]53
- 193[.]29[.]15[.]147
SHA-256
- 5d51dbf649d34cd6927efdb6ef082f27a6ccb25a92e892800c583a881bbf9415
- 907e1dfde652b17338d307b6a13a5af7a8f6ced93a7a71f7f65d40123b93f2b8
Remediation
- Block all threat indicators at your respective controls.
- Always be suspicious about emails sent by unknown senders.
- Never click on the links/attachments sent by unknown senders.








