

Rewterz Threat Alert – Fake NordVPN Website Used by Hackers to Deliver Banking Trojan
August 20, 2019
Rewterz Threat Intelligence Report 2019
August 20, 2019
Rewterz Threat Alert – Fake NordVPN Website Used by Hackers to Deliver Banking Trojan
August 20, 2019
Rewterz Threat Intelligence Report 2019
August 20, 2019Severity
Medium
Analysis Summary
Microsoft security researchers discovered an unusual phishing campaign which employs custom 404 error pages to trick potential victims into handing out their Microsoft credentials.
To do this, the attackers register a domain and instead of creating a single phishing landing page to redirect their victims to, they configure a custom 404 page which shows the fake login form.
This allows the phishers to have an infinite amount of phishing landing pages URLs generated with the help of a single registered domain.
The 404 Not Found page tells you that you’ve hit a broken or dead link.
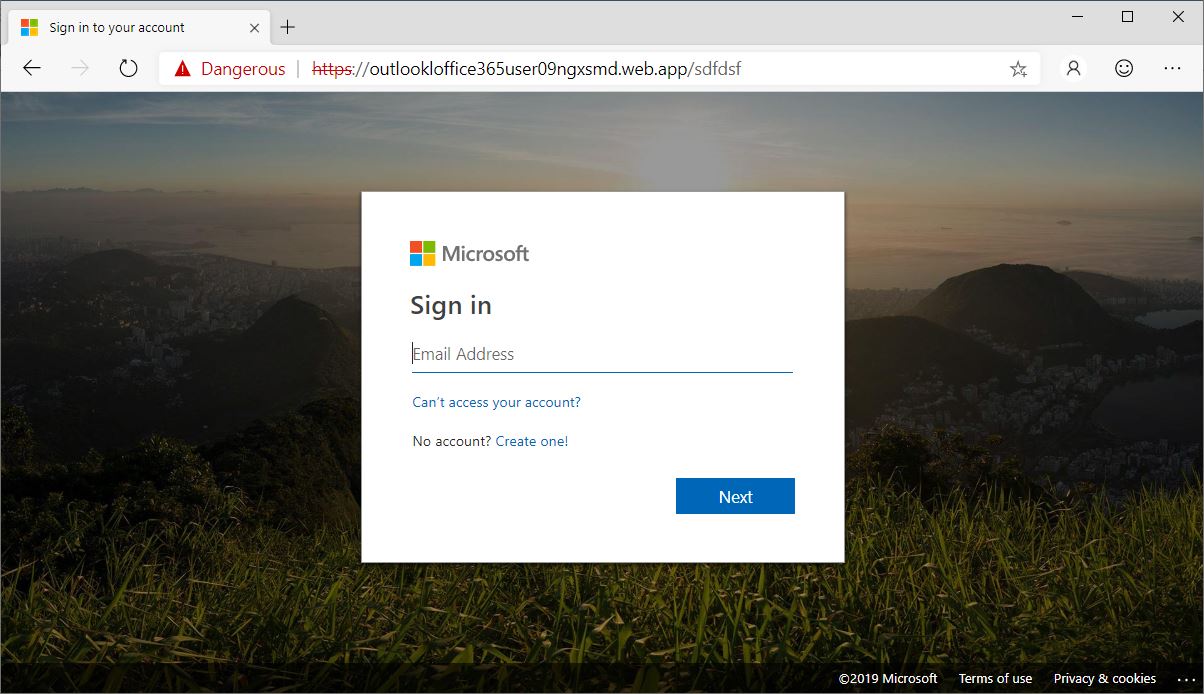
The custom 404 error pages these attackers use to harvest their victims’ credentials are perfectly camouflaged as legitimate Microsoft account sign-in pages, down to the smallest details.
All the links on the phishing page, including the ones at the bottom and the ones used to access one’s Microsoft account and to create a new one, are directing straight to official Microsoft login forms in an effort to make targets less suspicious.
The only elements missing from the phishing page are the “Sign-in options” link above the “Next” button and the cookies notification at the top of the page.
Impact
Credential theft
Affected Vendors
Microsoft
Remediation
- Always be suspicious about emails sent by unknown senders.
- Never click on the link/attachments sent by unknown senders.








