
Severity
High
Analysis Summary
Hancitor is an information stealer and malware downloader commonly associated with threat group TA511. In recent months, this actor began using a network ping tool to help enumerate the Active Directory (AD) environment of infected hosts. In October 2020, Hancitor began utilizing Cobalt Strike and some of these infections utilized a network ping tool to enumerate the infected host’s internal network. Normal ping activity is low to nonexistent within a Local Area Network (LAN), but this ping tool generates approximately 1.5 GB of Internet Control Message Protocol (ICMP) traffic as it pings more than 17 million IP addresses of internal, non-routable IPv4 address space. The actor pushing Hancitor has displayed consistent patterns of infection activity
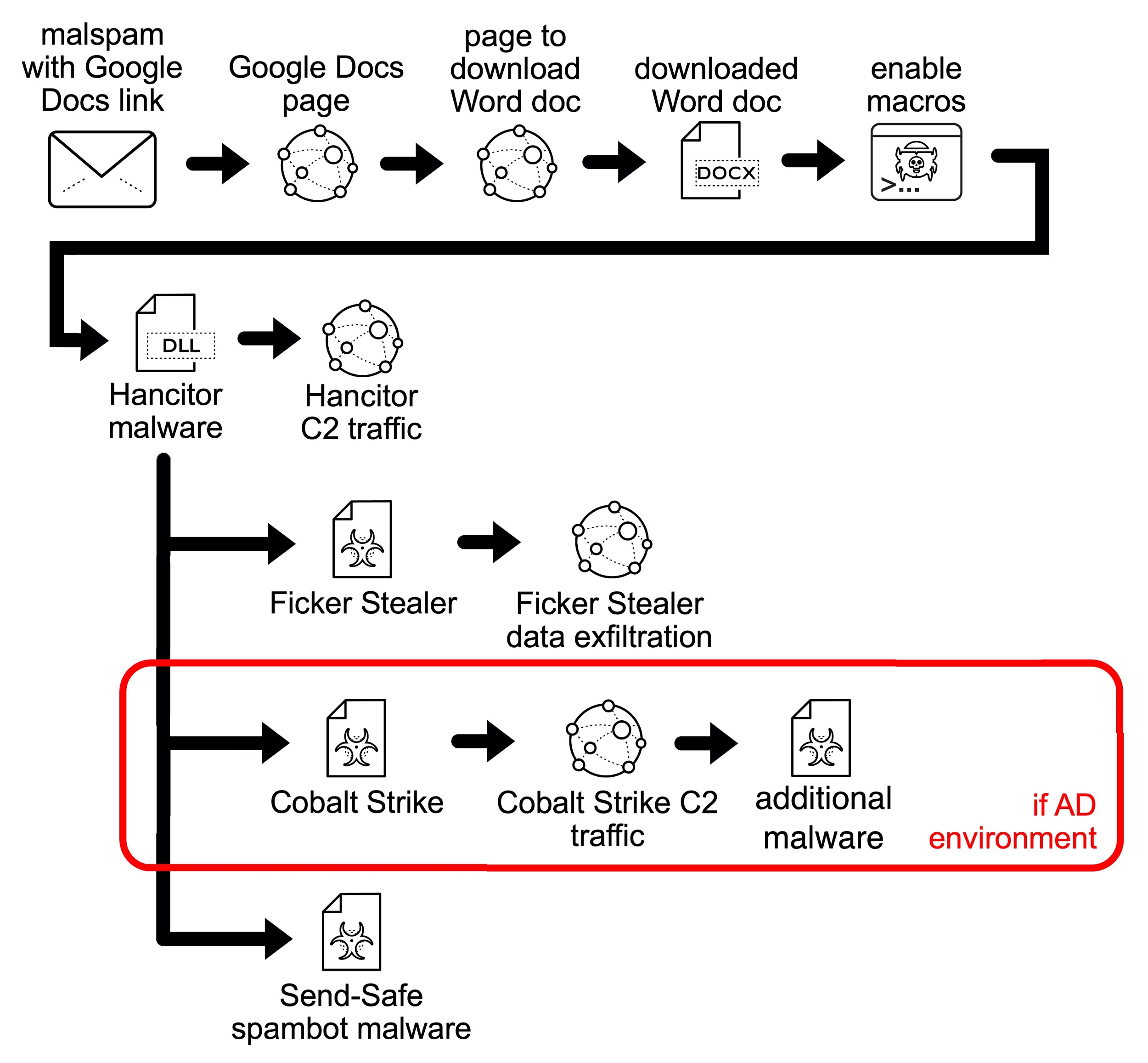
The chain of events for recent Hancitor infections is:
- Email with link to a malicious page hosted on Google Drive.
- Link from a Google Drive page to a URL that returns a malicious Word document.
- Enable macros (per instructions in Word document text).
- Hancitor DLL is dropped and run using rundll32.exe.
- Hancitor generates command and control (C2) traffic.
- Hancitor C2 most often leads to Ficker Stealer malware.
- Hancitor C2 leads to Cobalt Strike activity in AD environments.
- Hancitor-related Cobalt Strike activity can send other files, such as a network ping tool or malware based on the NetSupport Manager Remote Access Tool (RAT).
- In rare cases, a Hancitor infection follow-up is seen with Send-Safe spambot malware that turned an infected host into a spambot pushing more Hancitor-based malspam.
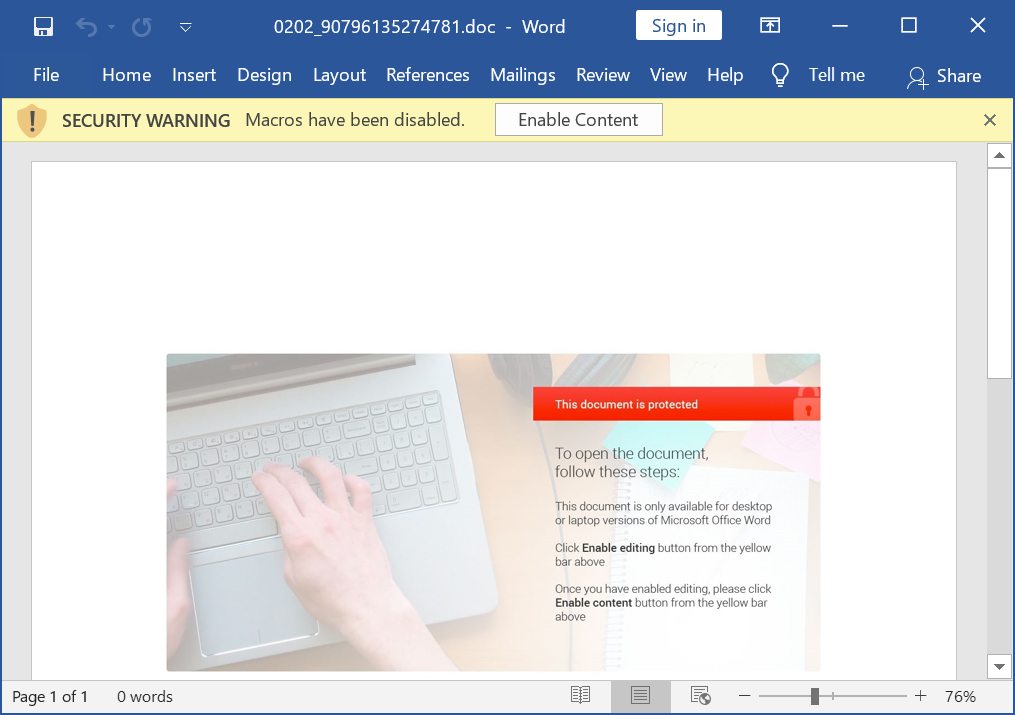
Given above is a malicious word document containing Hancitor DLL. When macros are enabled for these malicious Word documents, the macro code drops and runs a malicious DLL file for Hancitor. The DLL file is contained within the macro code.
Impact
- Information Theft
- Network-wide Infection
- Data Exfiltration
Indicators of Compromise
SHA-256
- 3b547e3bd5f3040c824ea497f265bf355483cce29c4e059d16e04fba20325498
- efc00db9c76fdbe84af2407b4cc94bbafaa06212176241606db3d11380f22738
- 94e60de577c84625da69f785ffe7e24c889bfa6923dc7b017c21e8a313e4e8e1
- 51ca66a8ac7f4e072b39ef886d7d414d6c6868d0d67a46150835297e65493dc6
- 2b3db85b06b60f46d03efc5e354fe0b36d19351e82d116d528a73203acadea66
- c314c08ebaf43ecdea2ea65787670bbb0578ce4c5f8e65d0351e320b2b3bcdf9
- b329abb04f60c258119ffdd7e0f9c7f4fef3afb673d6440cf2d1eb2d1602640b
- e41e0e22b8639f864d9a3b08daa53488ac2519277126774a6499d7675cfe401d
- bd93d88cb70f1e33ff83de4d084bb2b247d0b2a9cec61ae45745f2da85ca82d2
URL
- http[:]//allanabolicsteam[.]net/nedfr_[.]exe
- http[:]//alumaicelodges[.]com/fls[.]exe
- http[:]//anabolicsteroidsbuy[.]info/nedfr[.]exe
- http[:]//canadiantourismroundtable[.]com/hajdfjadf[.]exe
- http[:]//gade4senate[.]com/dfgg45g[.]exe
- http[:]//gadebrigade[.]com/783s[.]exe
- http[:]//gadeforsenate[.]com/sjh7843[.]exe
- http[:]//gadeforussenate[.]com/uiwuih43[.]exe
- http[:]//trustpilot-scam[.]com/32453[.]exe
- http[:]//wesleydonehue[.]org/dfggsdgrgs[.]exe
- http[:]//wheredidmarkmakehismoney[.]com/f5[.]exe
- http[:]//baadababada[.]ru/6jhfa478[.]exe
- http[:]//backupez[.]com/6yudfgh[.]exe
- http[:]//belcineloweek[.]ru/6hyuyj[.]exe
- http[:]//belcineloweek[.]ru/6sufiuerfdvc[.]exe
- http[:]//bobcatofredding[.]com/6lavfdk[.]exe
- http[:]//buckeyesecurity[.]net/6lajhbjyuk[.]exe
- http[:]//drivewaysnowservice[.]com/6gfbd5ws[.]exe
- http[:]//g1smurt[.]ru/6jiuu8934u[.]exe
- http[:]//kilopaskal[.]ru/6jhfa478[.]exe
- http[:]//klaustrofebia[.]ru/6jhfa478[.]exe
- http[:]//myinstabuzzz[.]co/6hyuyj[.]exe
- http[:]//mymooney[.]ru/6fwedzs3w3fg[.]exe
- http[:]//nvgeeforsegt[.]ru/6jhfa478[.]exe
- http[:]//onlybamboofabrics[.]com/6gdwwv[.]exe
- http[:]//pirijinko[.]ru/6jkiuwf43[.]exe
- http[:]//roanokemortgages[.]com/6lhjgfdghj[.]exe
- http[:]//sromecorlduce[.]ru/6sfsgfsgqwert[.]exe
- http[:]//sungardspo[.]com/6lhjgfdghj[.]exe
- http[:]//try-dent[.]net/6gdwwv[.]exe
- http[:]//wouatiareves[.]ru/6hy67438ue[.]exe
- http[:]//backupez[.]com/47[.]exe
Remediation
- Block the threat indicators at their respective controls.
- Do not visit links given in untrusted emails, even if they redirect to Google Drive.
- Do not enable macros for files downloaded unintentionally.








